On February 23, 2023 Shira Shamban and Vandana Verma gave a session about popular challenges in cloud security, and successful mitigation strategies.
If you’ve missed the session and wish to watch it, visit EliteCISO’s Youtube channel here. The event was followed by a Q&A session. Due to high participation we couldn’t answer all questions live, so we’ve decided to share this blog with answers to the questions we didn’t have time to answer. The Blog has 3 sections, to make it easier for you to focus on what matters to you:
- Security processes
- IAM Permissions, Shared Responsibility Model and Liability
- Solvo
Security Processes
Q: Some of the challenges discussed are covered by documentation, the real challenge is implementation and validation. What do you think?
A: Proper documentation can help prevent misconfigurations and docs are updated as part of the process. ISO mandates all changes to be recorded.
Like in many other security processes, documentation is an important part but not the only important part. Documentation is important for knowledge and best practices sharing, along with understanding of our application, processes and procedures.
It’s important because one of those days we will ask ourselves
Q: “why did we do it this way?” or “how did the team do it before?”.
A: The documentation will help us to create relevant tests and validations, to make sure our data and secrets are protected, that our authentication mechanisms work as expected and allowed actions are ran by allowed entities.
Changes in security IAM policies are good to document for a few reasons:
- Know when a certain change was made
- Know what change specifically was made
- Be able to revert if necessary
- Have a log to investigate in case of a potential incident
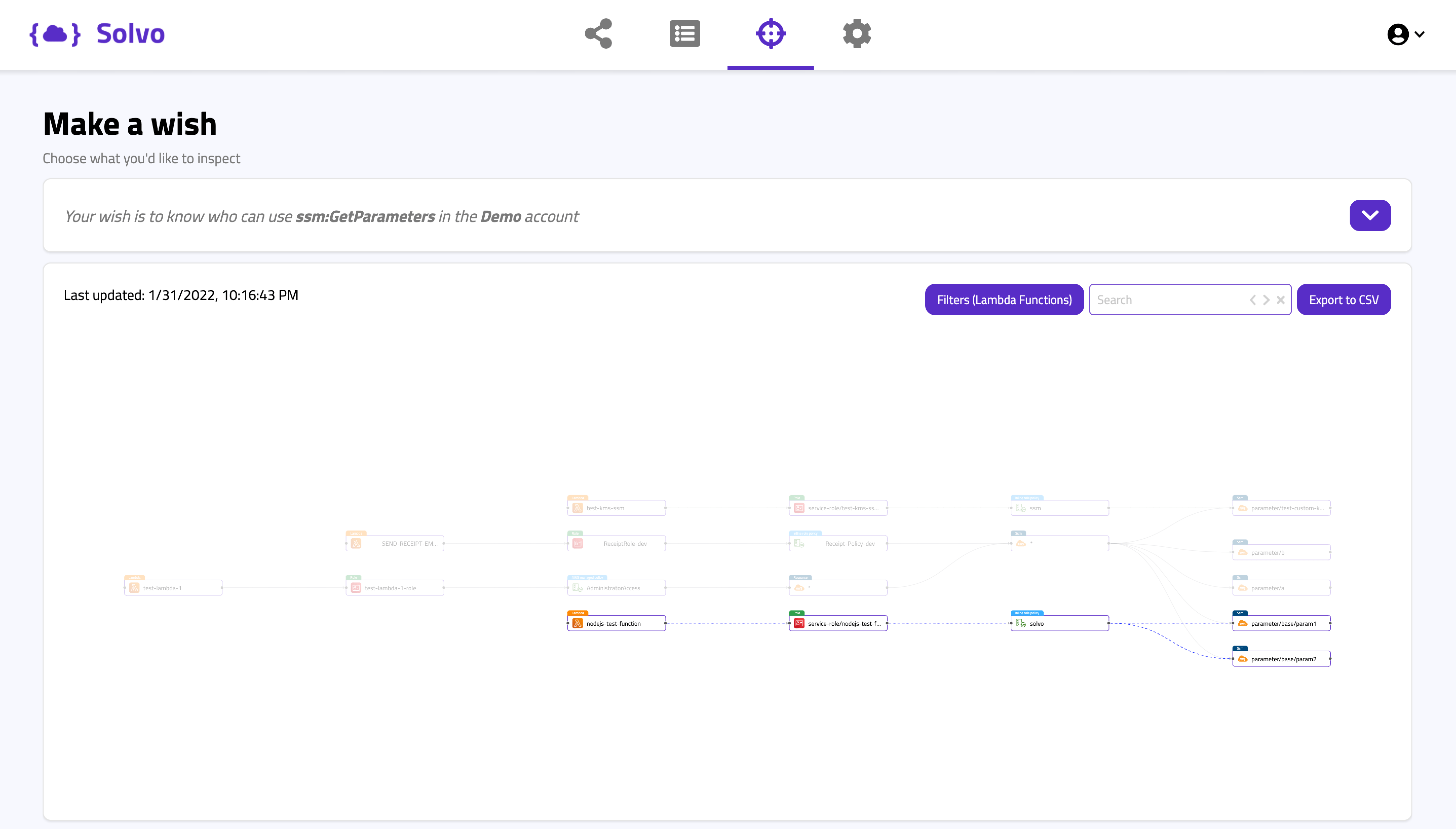
Logging of policy changes can be done in your ticketing system (like Jira), in a document or in Solvo’s timeline.
Q: Companies harden the external security landscape, but forget about internal security, one lope hole and threat actor go wild doing lateral movement. How do you suggest handling this?
A: This is very true and unfortunately many security practitioners don’t put enough attention on this. Security strategy is based on layers, because we always assume that at some point, one of the layers will get cracked and exploited.
We can create the best and tallest fences on the external perimeter, but it’s enough for one engineer to fall for a phishing campaign to get an attacker in your cloud account. And then what? If you don’t take good control of the permissions and access controls from within the cloud account and application, it’s game over.
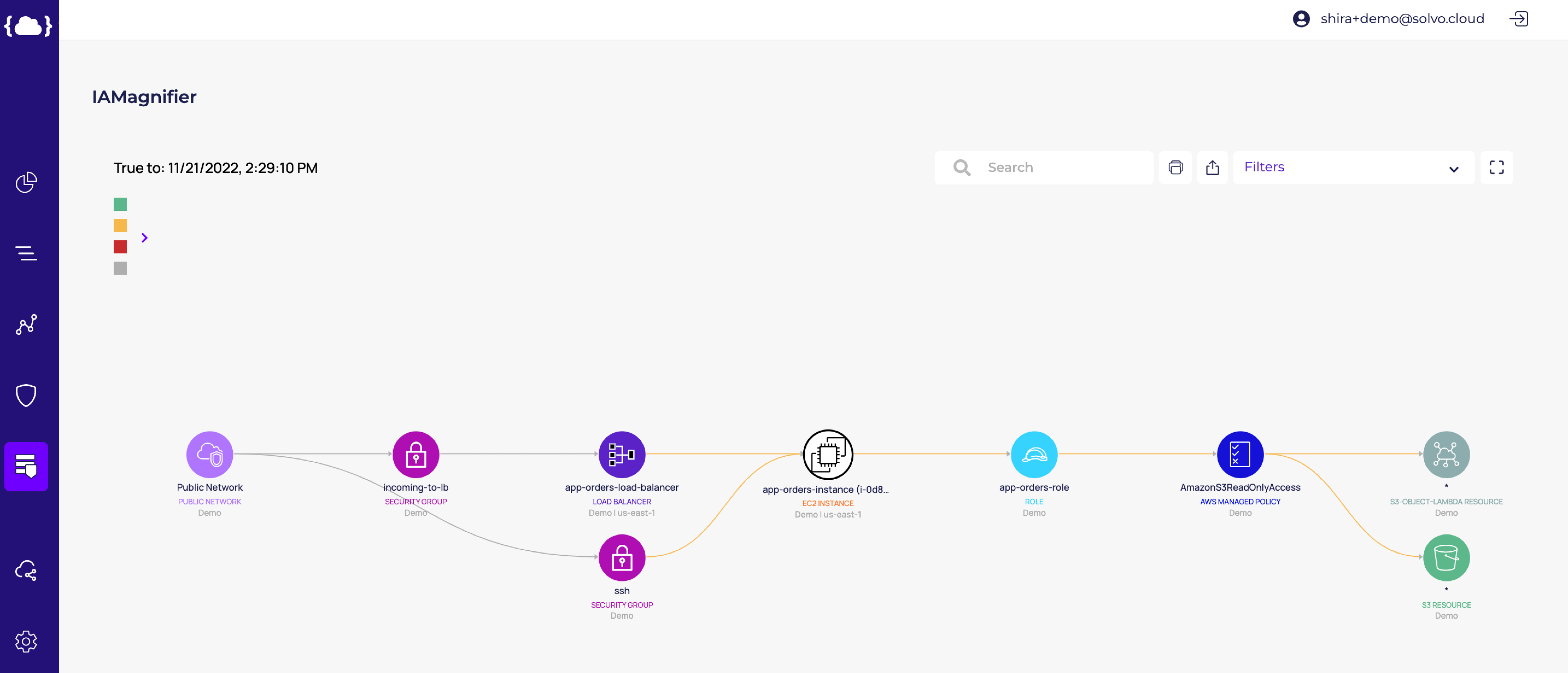
That’s why we need to understand the architecture of the application, and the places where we should put controls and guardrails, based on the risks and crown jewels.
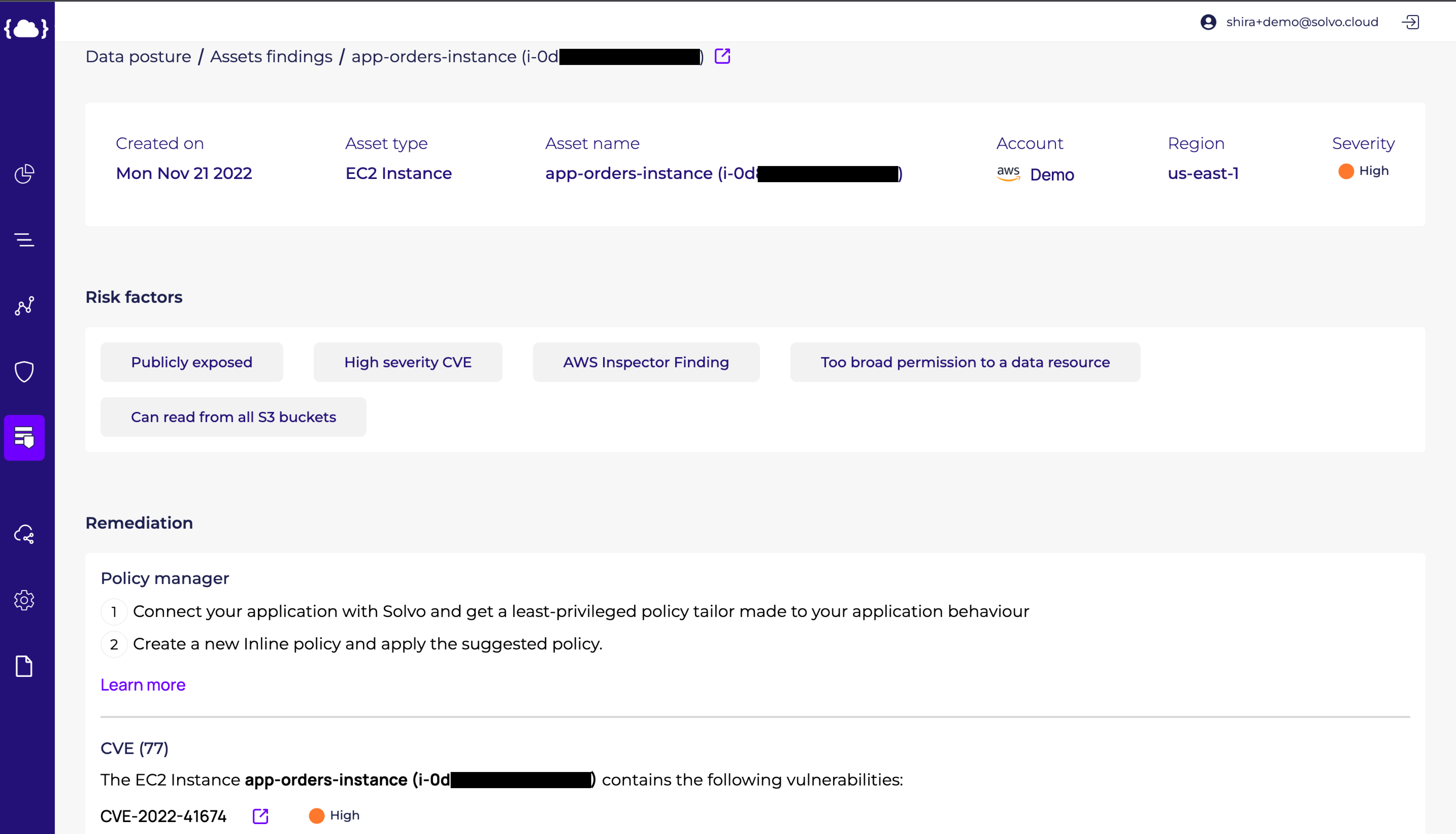
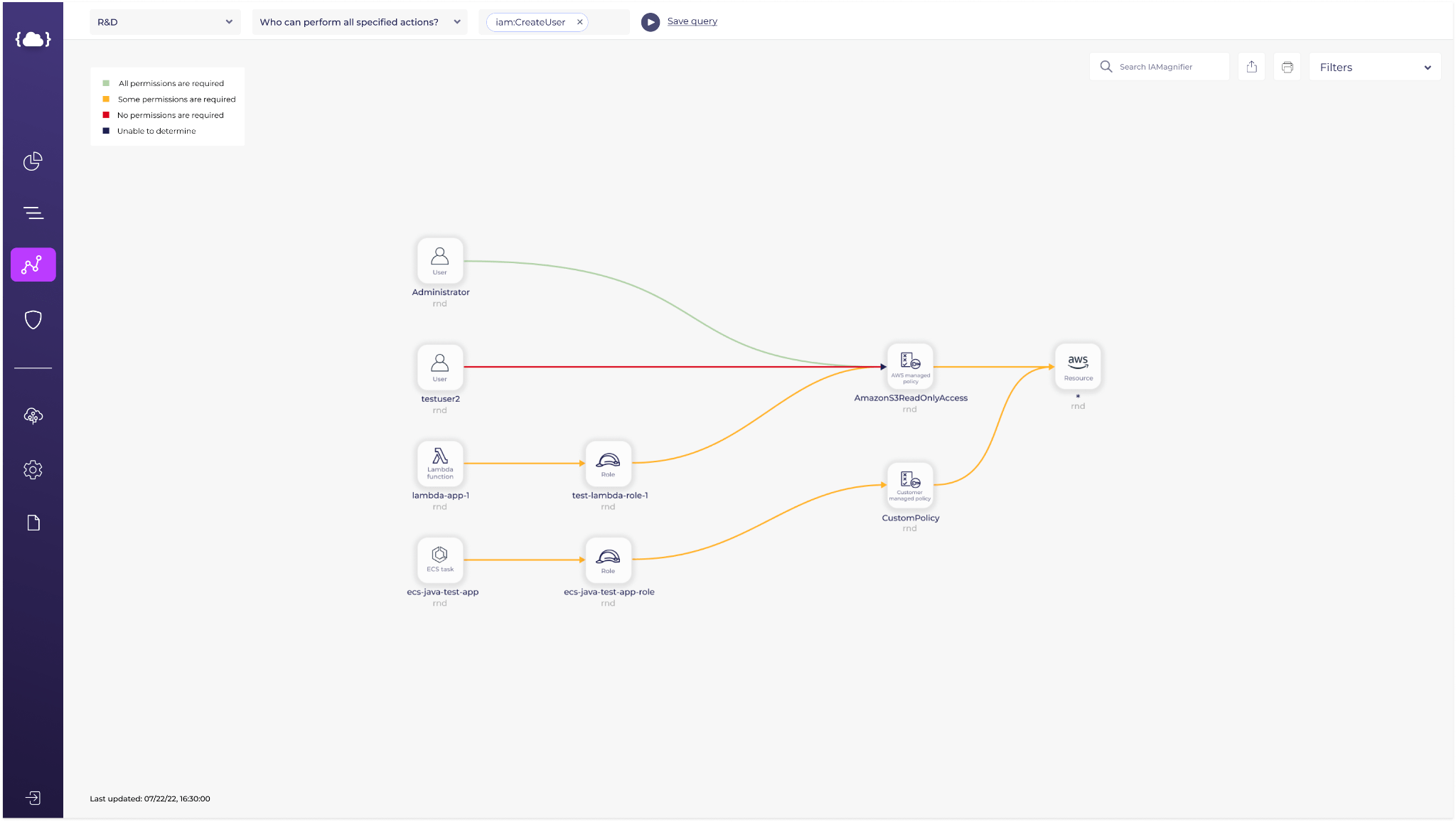
For example, if you have an instance with full access to all of your S3 Buckets, while it only needs a specific read permission from one S3 Bucket, by allowing the full access you’re creating a huge attack surface.
That is why you need to create a specific IAM policy, allowing that instance the specific access it needs, to the specific resource.
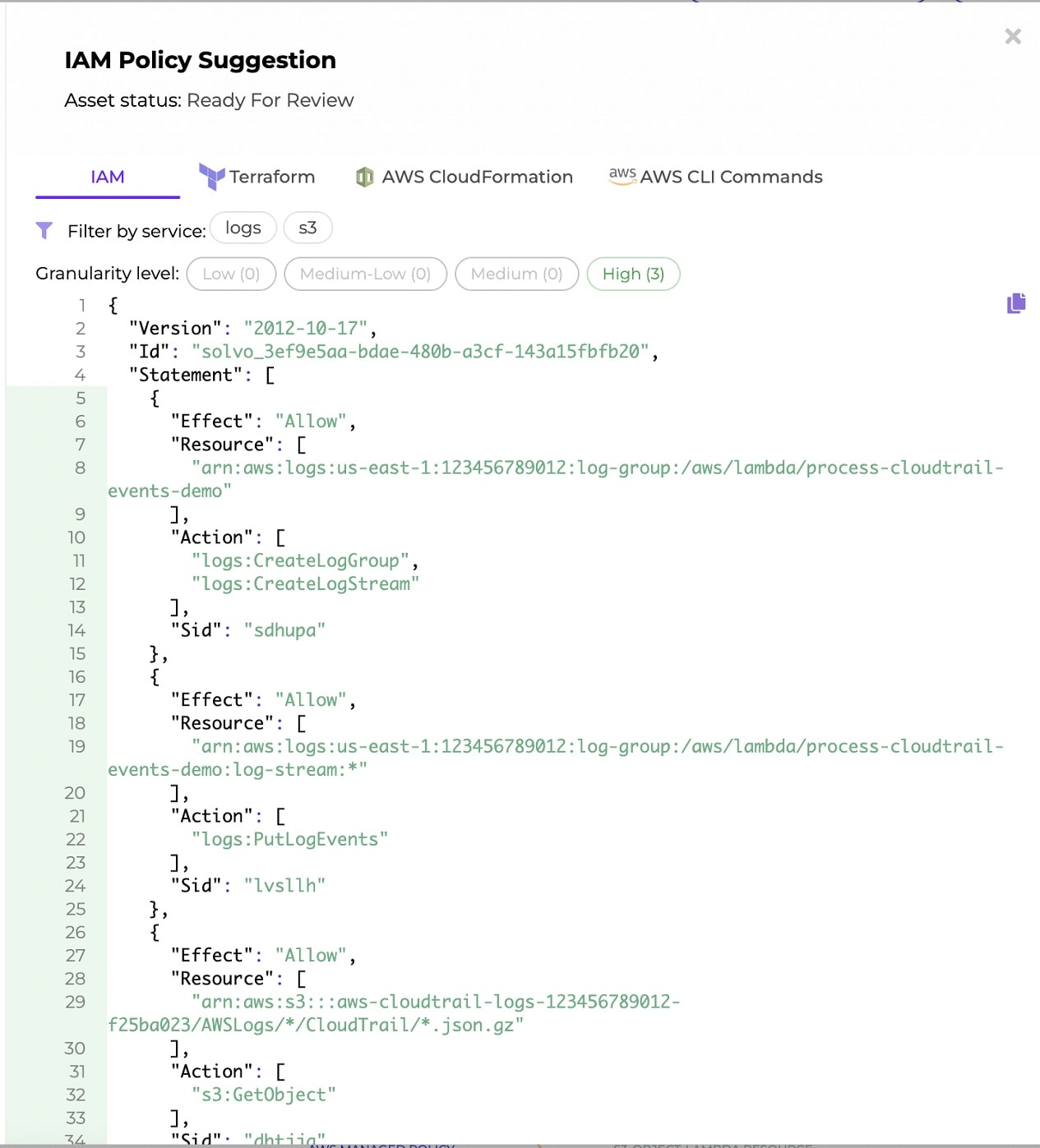
Solvo is generating applications-aware IAM policies, for all cloud components, automatically. Making it very easy to become least-privileged and compliant and maintain that status all year long.
Q: How do I solve the IAM issues if I have deployments spread globally and I am using a hybrid-cloud-architecture? How do I handle local regulatory requirements?
A: Compliance regulations change from one geography to another. Even though that means we need to become familiar with unique requirements, sometimes a process we did for one framework helps us with other, similar frameworks.
For example, the CPRA regulation that came into effect January 1st, 2023 is all about privacy of the residents of California, but it has some similarities to the GDPR. If you did a GDPR readiness process, the CPRA process will be fairly quick and easy.
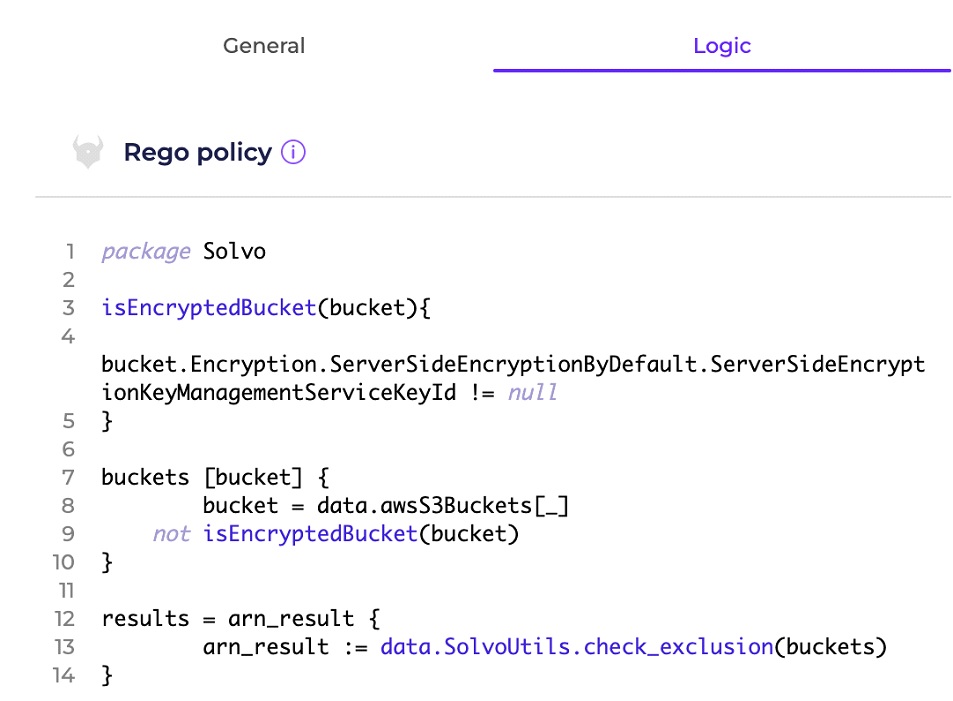
Solvo has a compliance module that is based on the OPA project.
This open-source enables you to easily create guardrails, based on compliance regulations or crazy ideas that you came up with. The rich ecosystem around it provides more rules that were written by other contributors, and supported by other security vendors.
This way, you can create one repository of compliance rules and implement it in different products.
IAM Permissions, Shared Responsibility Model and Liability:
Q: Can you shed some light on the security responsibility – where’s the line between the cloud user and the Cloud provider? Can you elaborate about the shared responsibility model including the indemnity and legal liability?
A: The shared responsibility model is an important principle to understand when using the cloud. I’ve heard people say “I put this data in the cloud and therefore it’s secured”. But this is the wrong approach.
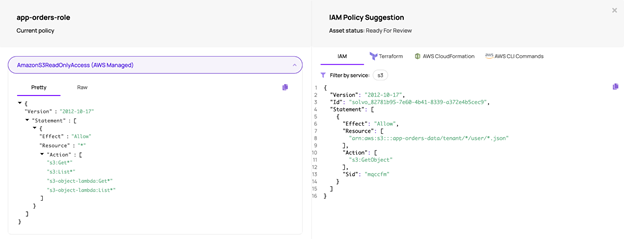
Cloud vendors are responsible for certain things, while we, the users, are responsible for others. It is up to us to configure the infrastructure correctly and make sure our code is secure. It’s worth mentioning that in December 2021 AWS had a security issue where the Support Service Role was granted with S3:GetObject permissions.
While according to AWS, it was impossible to exploit that permission, we need to understand that when using AWS managed policies, such things can happen. That is why using AWS managed policies is not a best practice.
What you should actually do is customize the IAM permissions based on the needs of your organization and application. This requires time, deep understanding of application logic and continuous maintenance.
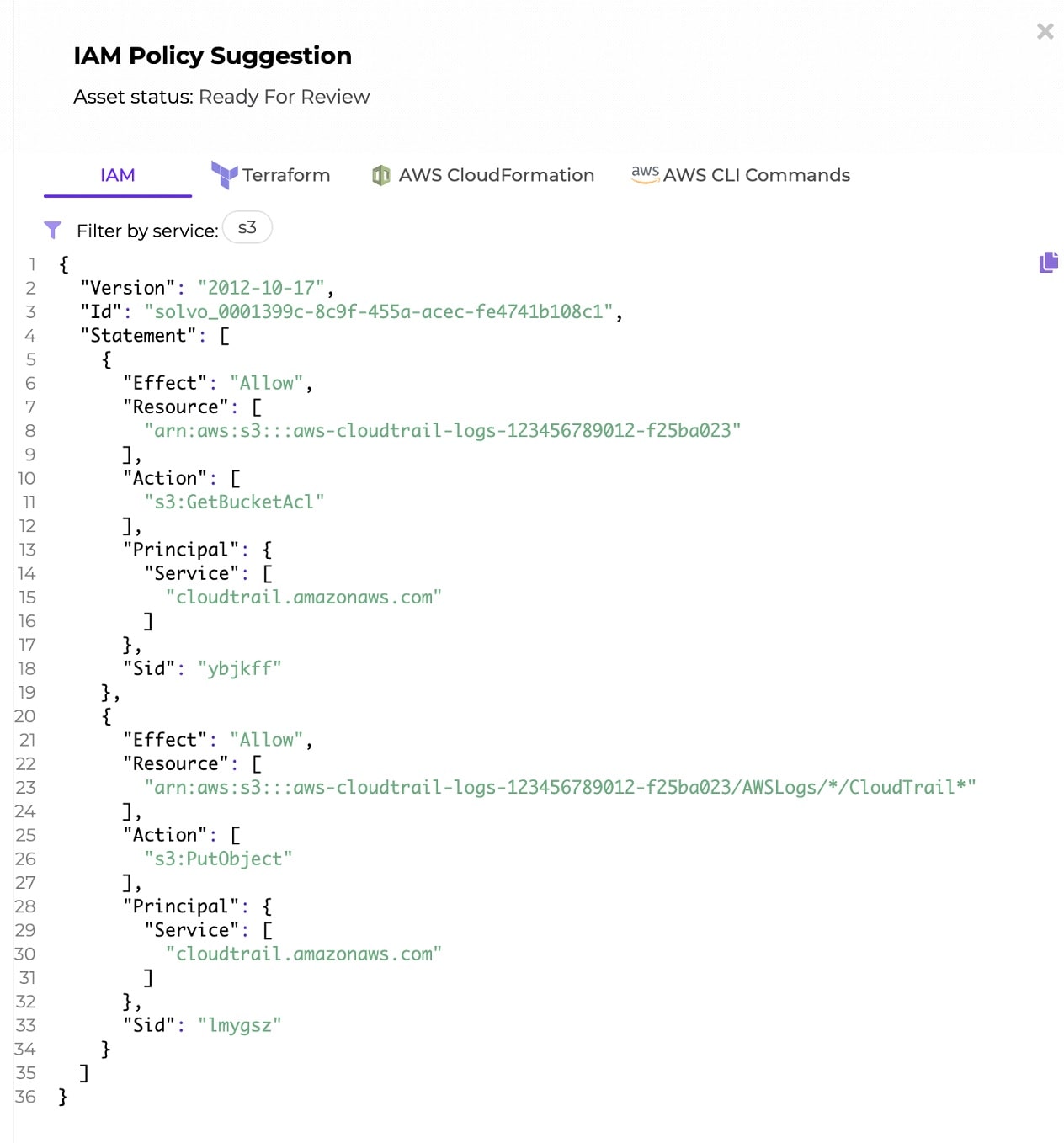
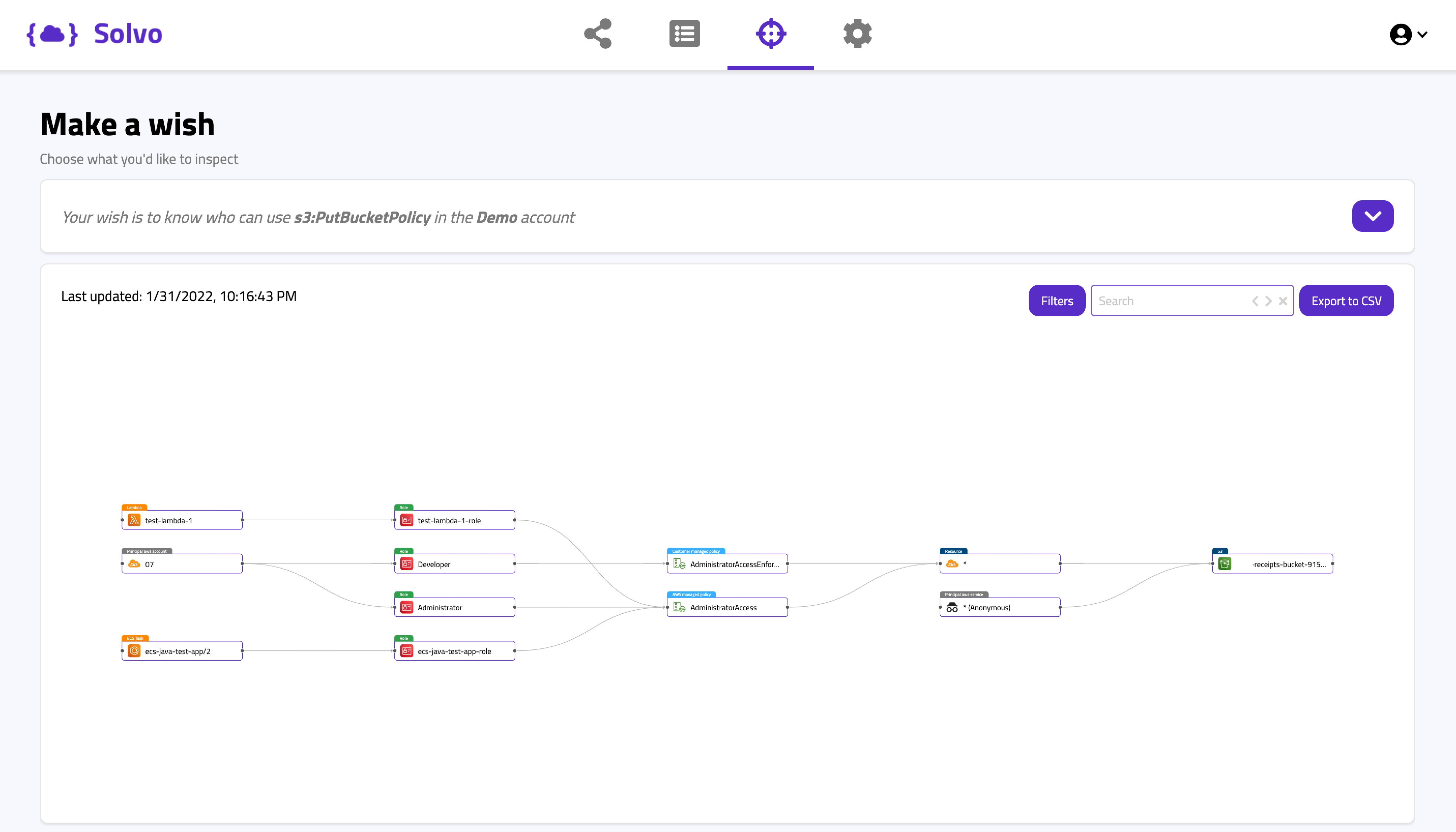
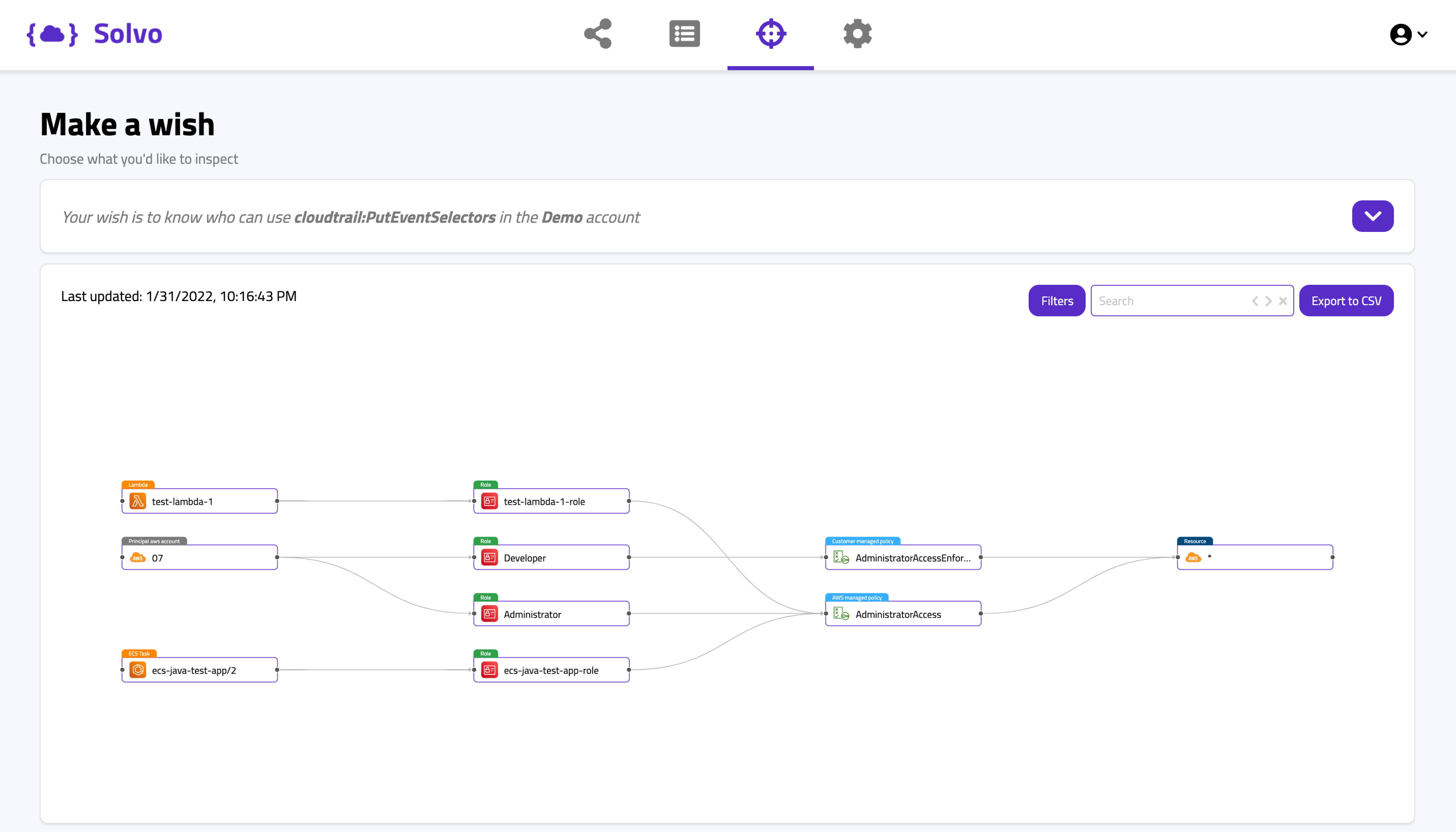
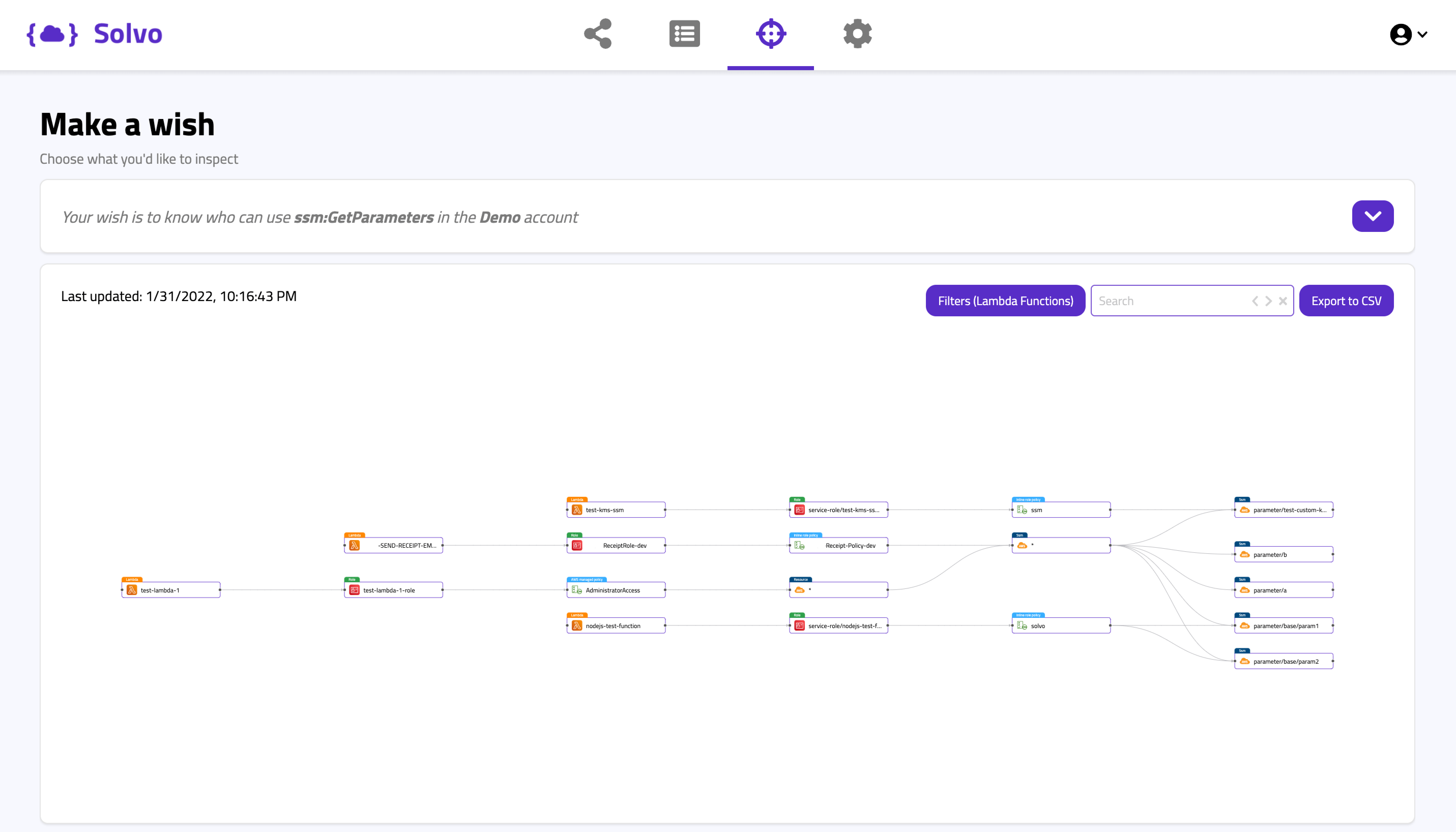
Solvo’s policy manager capability was created to do all the heavy lifting for you. By analyzing the behavior of the application, Solvo is able to understand what exact permissions are required, create them in IaC or CLI formats and ship them to the ticketing system of your choice for enforcement.
We make the process of understanding the app, building the policy and the maintenance automated and easy.
Q: I am a cyber risk insurance consultant and not a cyber risk professional. What are the best practices we need to adopt for IAM?
A: Thank you for creating awareness for cloud and data security in the risk insurance industry. There are some practices that are extremely easy to implement for you as a consultant, and that would help your customers to improve their security posture and resilience:
-
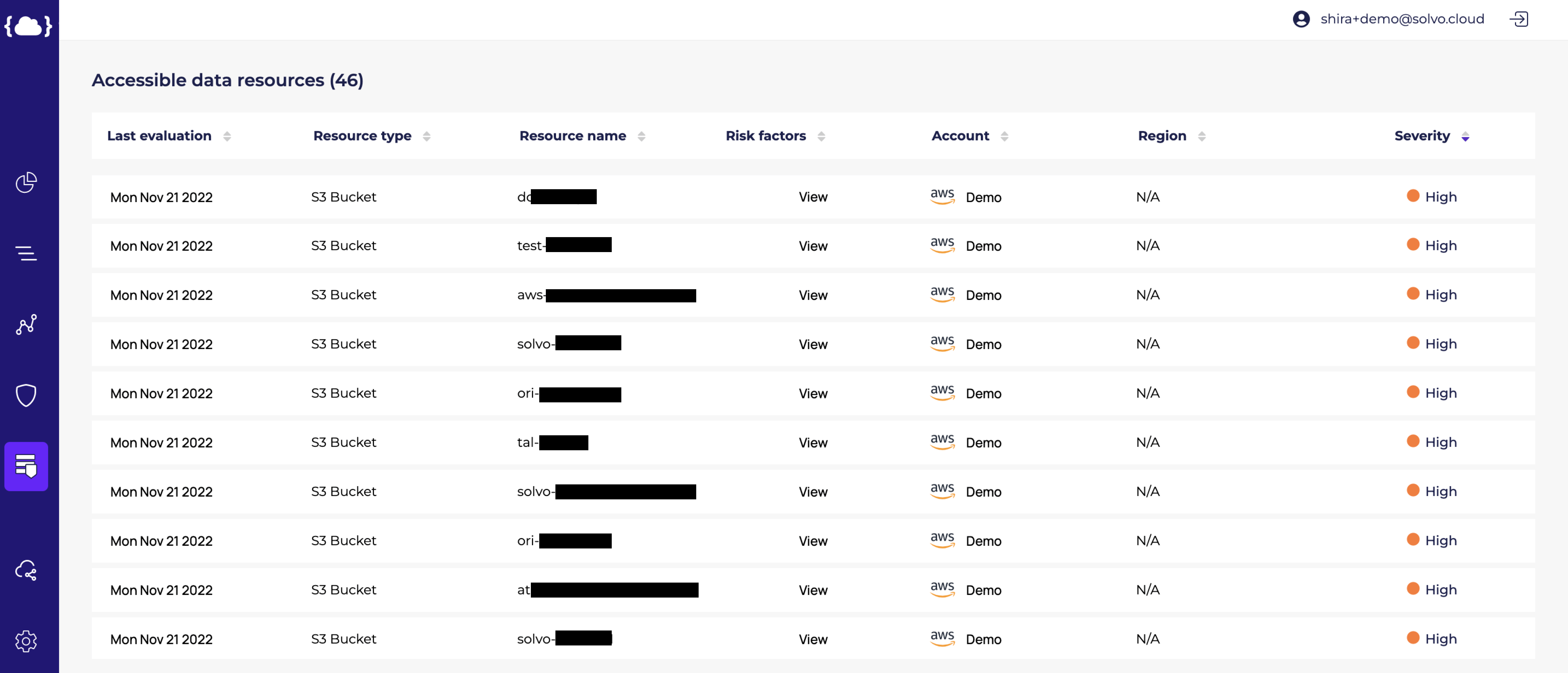
- List ALL data resources (even the ones that are called “test” or “research” and people think for some reason that are not important). We should assume all data resources are at risk to contain sensitive information.
- Know ALL admin and high privilege users and make sure they actually need those permissions.
- Create user groups and use them to grant permissions.
- Run a scan to see which resources have direct or indirect internet access.
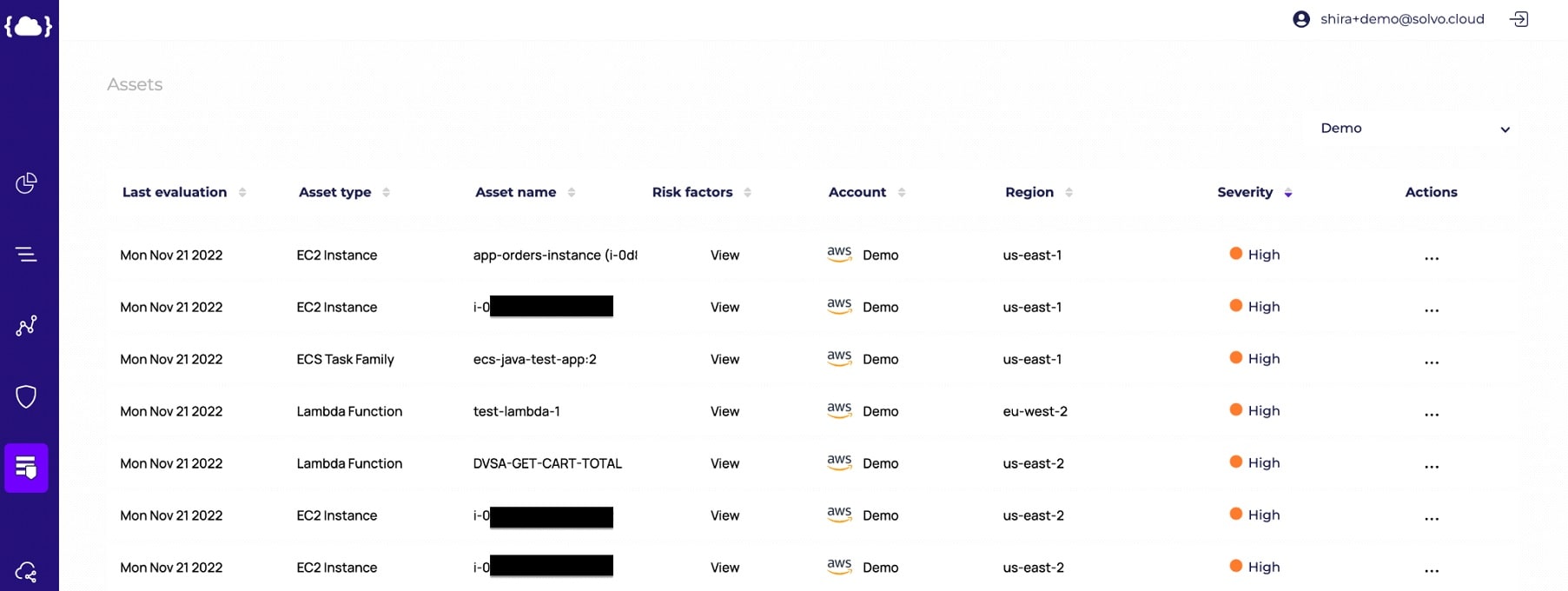
This short list of tests is the very basic checks I think you can and should run when meeting a customer. It doesn’t require deep DevOps capabilities and it will give you and your customer a good idea about their security posture. The next step is to encourage them to monitor changes and drifts from what we know, and put guardrails for specific violations.
Solvo is used by auditors and professional services companies to run periodic audits for their customers. In our Compliance Manager module, the auditor creates a bundle of rules that is relevant for his client, they can present the gaps, suggest remediations and even offer a monitoring service to make sure the good compliance posture we have is maintained and improved over time.
Very few of us do a continuous post-implementation review as part of SDLC. Either because we don’t have the right tools or don’t have enough bandwidth. Oftentimes, changes are made without a change approval process and these create gaps.
So from a policy documentation point of view we may have everything as expected but implementation fails. What is your best practice?
Q: How can we check suggested changes before applying them and before a possible security issue occurs?
Injecting Security Awareness is a cultural change and takes a long time.
A:There’s a tension between writing documents and protocols vs. implementing them and measuring their impact. What you’re saying is that you might write the best protocol or policy, but if it’s not implemented correctly we’re going to lose.
We like to stay that security is first and foremost an issue of culture, and making changes to culture is nearly impossible. If people don’t have security at mind they will not truly embrace the great protocol you wrote. That’s why we use security tools that hopefully will integrate well with our existing flows and will help us to achieve the missing parts.
When we started to build Solvo we knew we’re creating a security tool that has to work well with several types of users – security executives who want to get an overall picture, security engineers and DevOps who need to handle specific security issues and make infrastructure-related decisions, and developers who might need to enforce security policies in a way that fits their application.
We know we have to build a product that will not make the developers work very hard, but quite the opposite – will be super easy to onboard, will create the fix they need to enforce, and codify it for easy enforcement. Software should work for us and not the other way around.
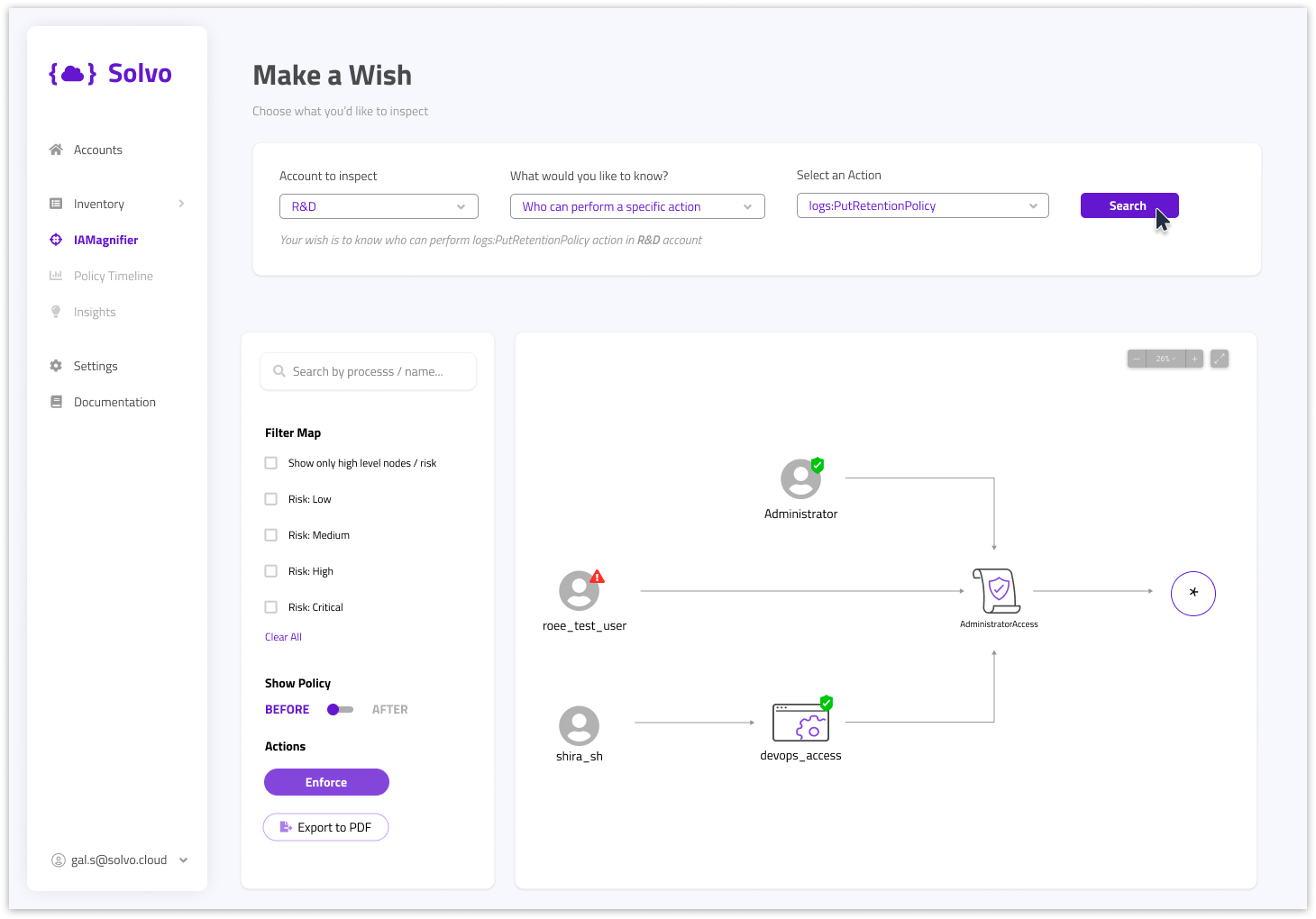
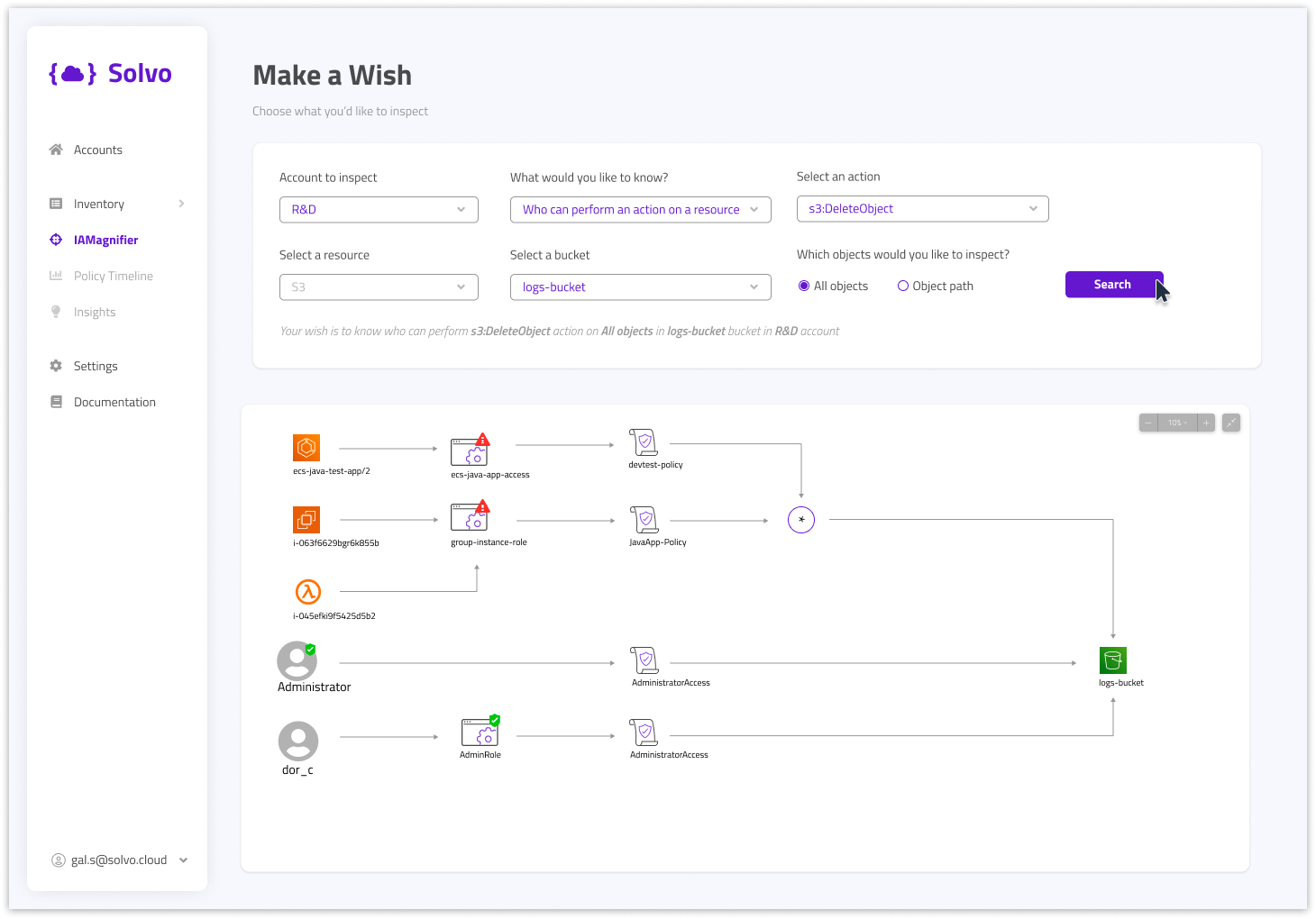
One of the capabilities in Solvo it to test the suggested security policy, this way the DevOps of security engineers can gain the confidence they’re making the right decision.
Most of the cloud breaches are due to a misconfiguration. We need to ensure secure configuration and also have processes (Automated & Manual) to identify gaps in configuration. What are the best practices? Gap analysis is key.
Agreed. It’s not enough to run an assessment before your SOC2 audit, because the day after you might realize that one of your team members forgot a sensitive S3 Bucket available from the internet. You need a continuous process that will check for violations and drifts, prioritize them based on the risks and blast radius they have in the account and hopefully suggest a remediation plan.
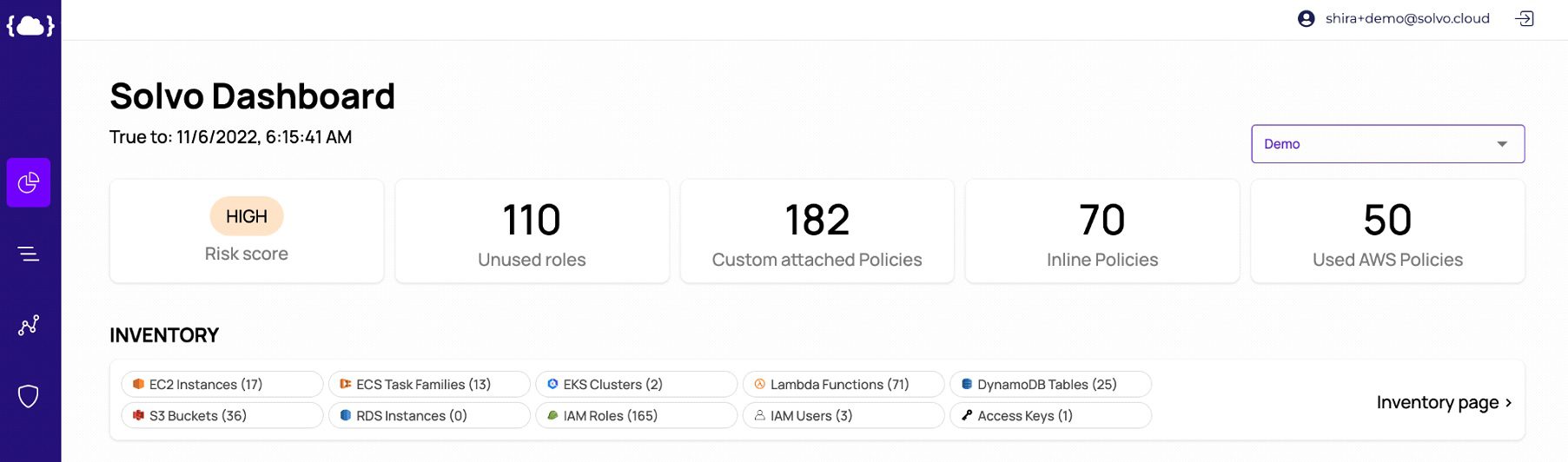
Solvo’s Posture Manager is doing just that. It continuously checks for violations, misconfigurations and vulnerabilities, correlates that with other risk factors to understand the potential impact on the cloud account, prioritizes findings so you know what’s critical, and also creates the remediation plan.
About Solvo:
Q: How is Solvo different from tools like Azure Sentinel? What additional features does it have?
Cloud vendors have some built-in security features. Each vendor has slightly different capabilities that compliment their infrastructure. Some products have configuration analysis (do you have any wildcards or open ports), some have vulnerability analysis (with an agent or by taking a snapshot and scanning it).
Solvo’s unique value is by analyzing both the infrastructure, and the application behaviour! This way, we’re able to identify misconfigurations, and to create new configurations based on the unique needs of the application.
Q: What should I use CASB, CWPP, CSPM, CIEM,CNAPP?
A: Those categories can get very confusing when looking at cloud security solutions. There are some overlaps and similarities between the categories, and one product might fit several categories.
Solvo is analyzing the cloud infrastructure configuration, the application behaviour, outputs from other security products you might be using and out of that produces the remediation. One thing Solvo doesn’t do is install an agent, or take snapshots of your resources. This is more secure and also cost effective.
Q: How is Solvo licensed?
A: Solvo is a SaaS offering, and pricing is tiered by the number of compute and data resources you have in your account. To get a price estimate, you can start a free trial here.
Q: In your experience, who owns Solvo in an org? Security team or SRE/Cloud team? If it’s the security team, it will act as a consulting engagement. Or SRE/cloud team, where security teams keep chasing them for patching issues. If it’s the SRE/cloud team, can Solvo be integrated within their workflow so they feel accountable for cloud security issues and it gets solved at earliest?
A: Solvo can accommodate several different use cases and help different teams, that all depends on the company structure and processes:
Security team – this team is usually responsible for the overall security posture, sometimes also compliance, and in recent years also data security. As Solvo users, the security team will observe the trends of security and compliance violations, get notified for critical vulnerabilities, misconfigurations and risks and also be able to create guardrails and standards that once in place, will let you change the security into developer-friendly ones.
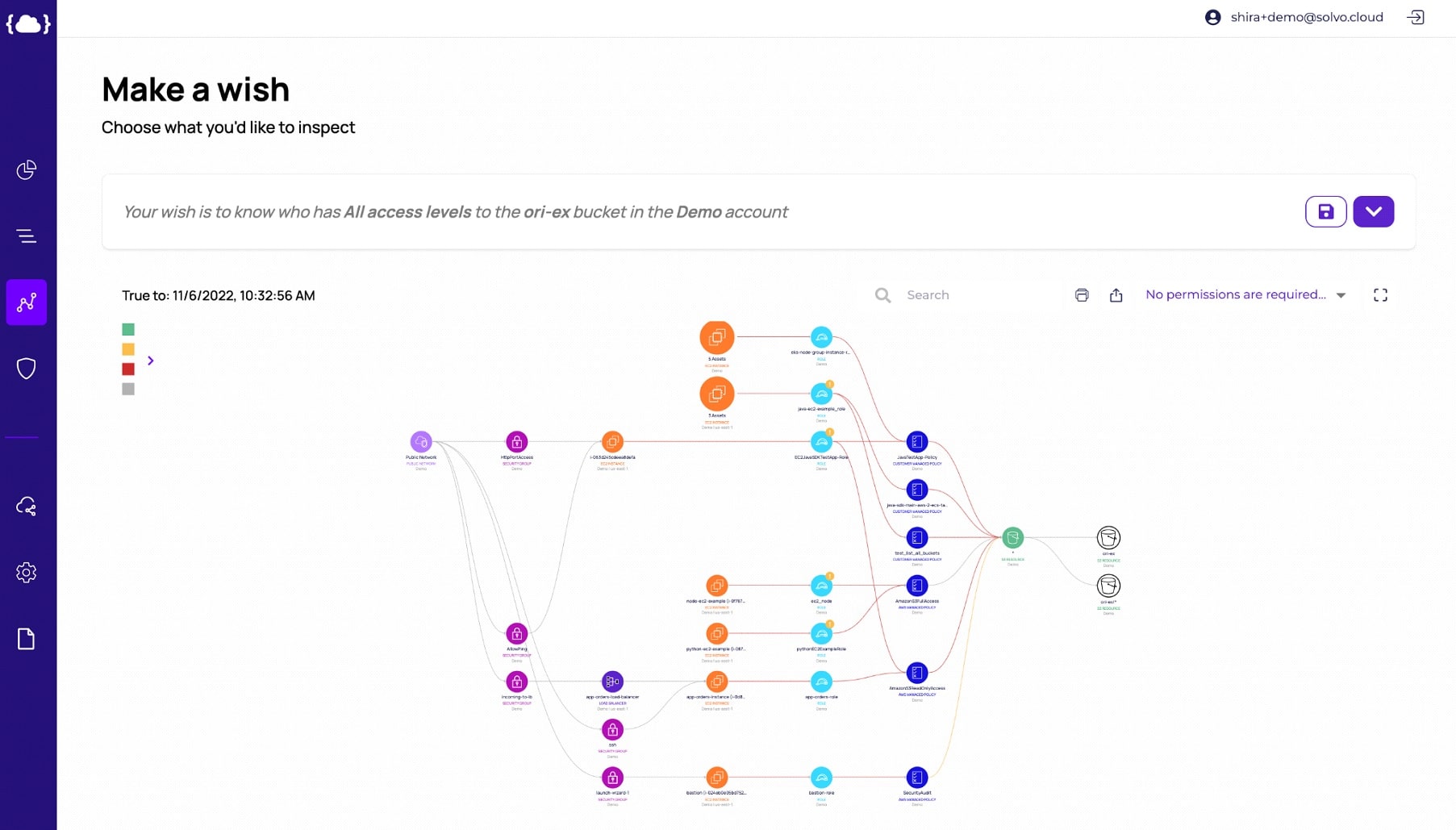
Solvo’s graphs make it easy to have a fruitful conversation between security and other teams and partners, when everyone sees the components, applications and actual use on one screen.
SRE / Cloud team – this team is responsible for the overall infrastructure availability, stability and scalability. They will need to resolve misconfiguration issues that were found by any security product that you use.
Solvo is generating the remediation for these findings, as IaC or CLI command. That’s why, integrating Solvo with the existing CI/CD processes to resolve them quickly and efficiently. With Solvo the team can see the existing security configuration, the suggested / ideal configuration, and a test capability to check the suggestion.
R&D team – this team is not only responsible for writing and shipping code, today writing a cloud application includes making changes to the infrastructure. When a security issue is detected, the app owner will decide how to handle it, with the help of the security and DevOps team.
By using Solvo, the team can understand who’s the app owner, prove which components are in the blast radius of the security issue, and get the remediation that will fix the problem and not break the app.
Q: I wanted to ask can Solvo be useful in the Indian Public Sector, which is still hesitant to go to the Cloud?
A: Many organizations still struggle with cloud adoption. Some need to migrate existing applications, while others wish to write new cloud-native applications but lack the knowledge of how to do it most efficiently.
For the migration use case, Solvo helps by saving hundreds of hours of redesigning the new security configuration the migrated application would require. Solvo analyzes the bahviour of the application and creates the new security configuration, thus helping to migrate easily and securely, while trusting the cloud.
For the cloud-native application, Solvo helps all teams to build a healthy security culture, holding users accountable while equipping them with the tools to help them make smart decisions faster.
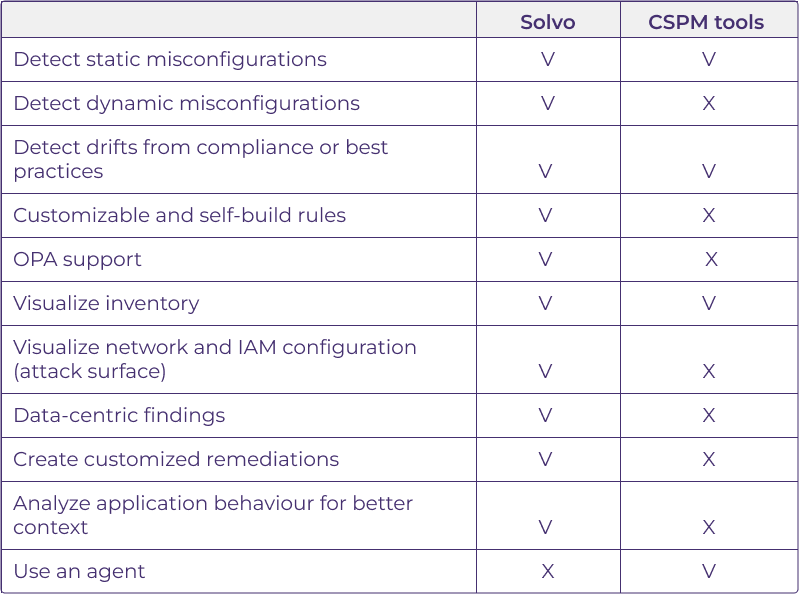
Q: What are Solvo’s benefits compared to other CSPM tools?
A: The differences are below. If we look of the core differences, these would be the application analysis provided by Solvo, along with the accurate remediation that saves time and reduces risks.