Cloud Security just got more colorful
Understanding your IAM permissions model is hard as is. Let alone when you need to manage production applications with hundreds of components and thousands of entitlements.
As a result, Solvo created a visualization tool called IAMagnifier.
We know that visualizing components and permissions is only the first step in creating a least-privileged security configuration, so we’re happy to introduce our color-coded permissions map!
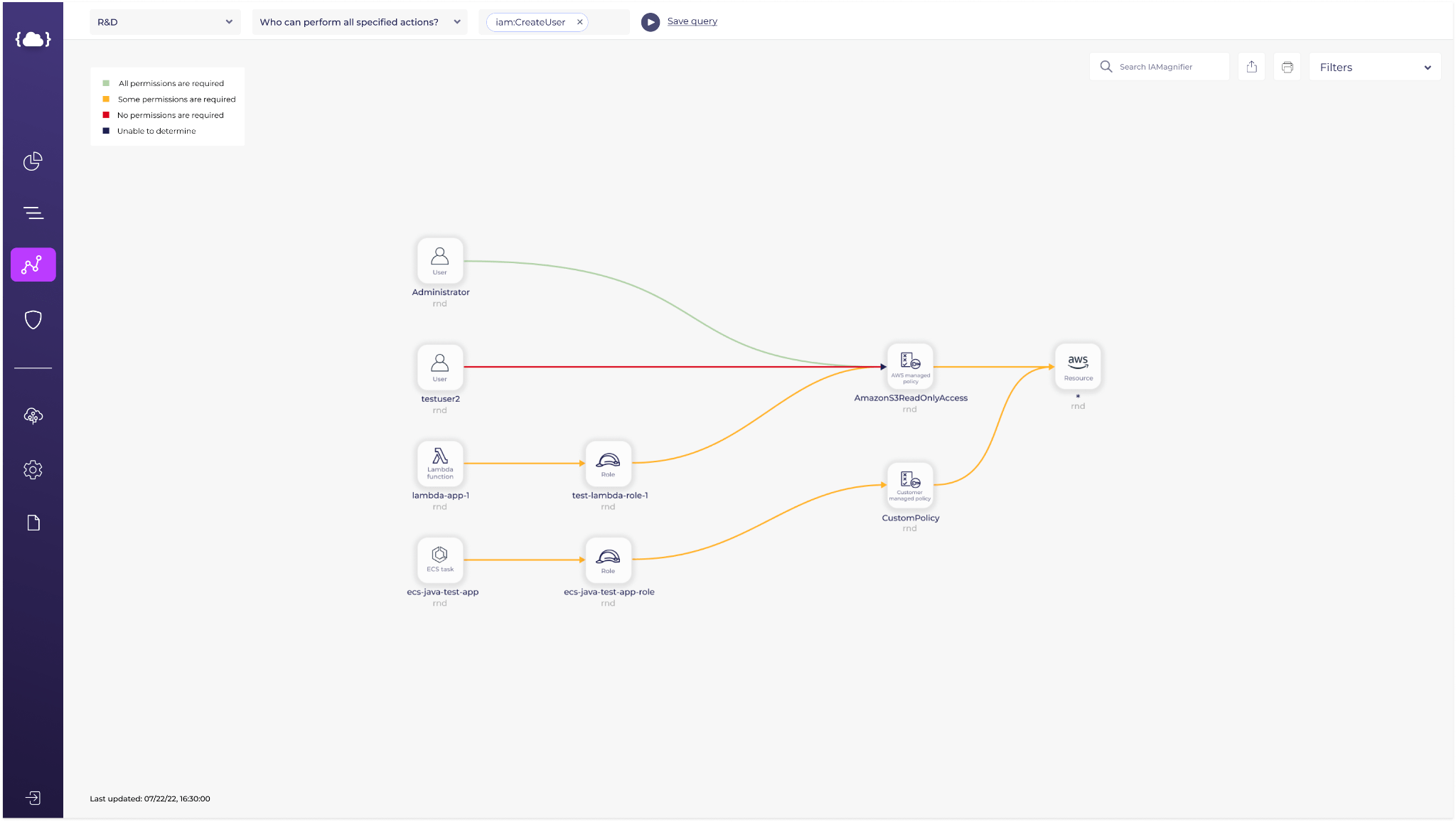
On this map, as before, you can see your cloud components (storage, compute assets, network assets, external accounts and users), along with the IAM roles and policies that enabled access between them.
Starting now, the access arches connecting those components will be highlighted in a color that describes their necessity, or how excessive this connection is.
As you recall, IAM permissions are not a yes / no kind of access. You can state specific resources and sub-resources, specify the necessary actions (read, write, delete, etc.) and even add conditions.
These permissions should be as granular and specific as possible to limit a blast radius should your account, credentials, components or users get compromised. The more granular – the better!
When highlighted in red – this connection is completely excessive. It was not used for a long time, or even never at all. Your application doesn’t need it in order to perform the actions you wanted it to perform. Go ahead and remove it.
When highlighted in green – you’re all set! This policy is well configured and only allows the necessary actions.
When highlighted in gray -More information is needed in order to provide a recommendation. You should be aware that in theory, an action between these connected components is possible, and if you think it shouldn’t be there, make the adjustments. It might also be that you can terminate these assets.
When highlighted in orange – this connection is necessary, but is too broad and can be fine-tuned and specified.
You’re probably wondering how to reduce this connection and make it less-privileged. But this is actually very easy. Just visit our Policy Manager page, and get the new IAM policy your component needs, in your favorite format (raw, Terraform, CloudFormation or CLI command).
Want to get your copy of a green-looking IAM map? Start a free trial, fix your misconfigured IAM policies and be the CISO’s hero!