Cloud data security is a hot topic these days. According to a Cloud Security Alliance report, 67% of organizations host sensitive data or workloads in the public cloud.
This leads me to believe that the other 33% don’t actually know that they are storing sensitive data in the cloud.
Data security becomes a major concern when it is not handled and protected in the appropriate manner which leads to the possibility of your data being stolen, encrypted and held for ransom, and published online. All of these might lead to business disruption, money loss and fines to be paid.
In the cloud, it’s important to understand that protecting a specific data resource or blocking its internet access is simply not enough. Based on the security configuration of the cloud components (users, cloud resources), gaining access to a data resource from the internet, whether from an external cloud account or via another misconfigured entity, is still possible.
So, how do you get a hold of the security posture of cloud resources and the risk they impose on data resources? Solvo is thrilled to announce the release of Data Posture Manager (or DPM)!
We know that security products create excess noise and stress when producing various alerts and notifications thus adding to the existing alert fatigue and creating more anxiety.
This is why the DPM is equipped with an advanced scoring algorithm, prioritizing the findings based on: vulnerabilities, IAM permissions of the data resource, the connected resources (depending on how accurate or excessive they are) and, direct and indirect network access, blast radius, and business impact.
This unique scoring mechanism is different from what you’re used to using in other products. Instead of a static and predefined score per violation, the DPM’s scoring algorithm is dynamic and takes into consideration different parameters to provide the most relevant findings first.
These prioritizations allow the security team to focus and spend their time on specific issues that will have the most impact on the overall security posture.
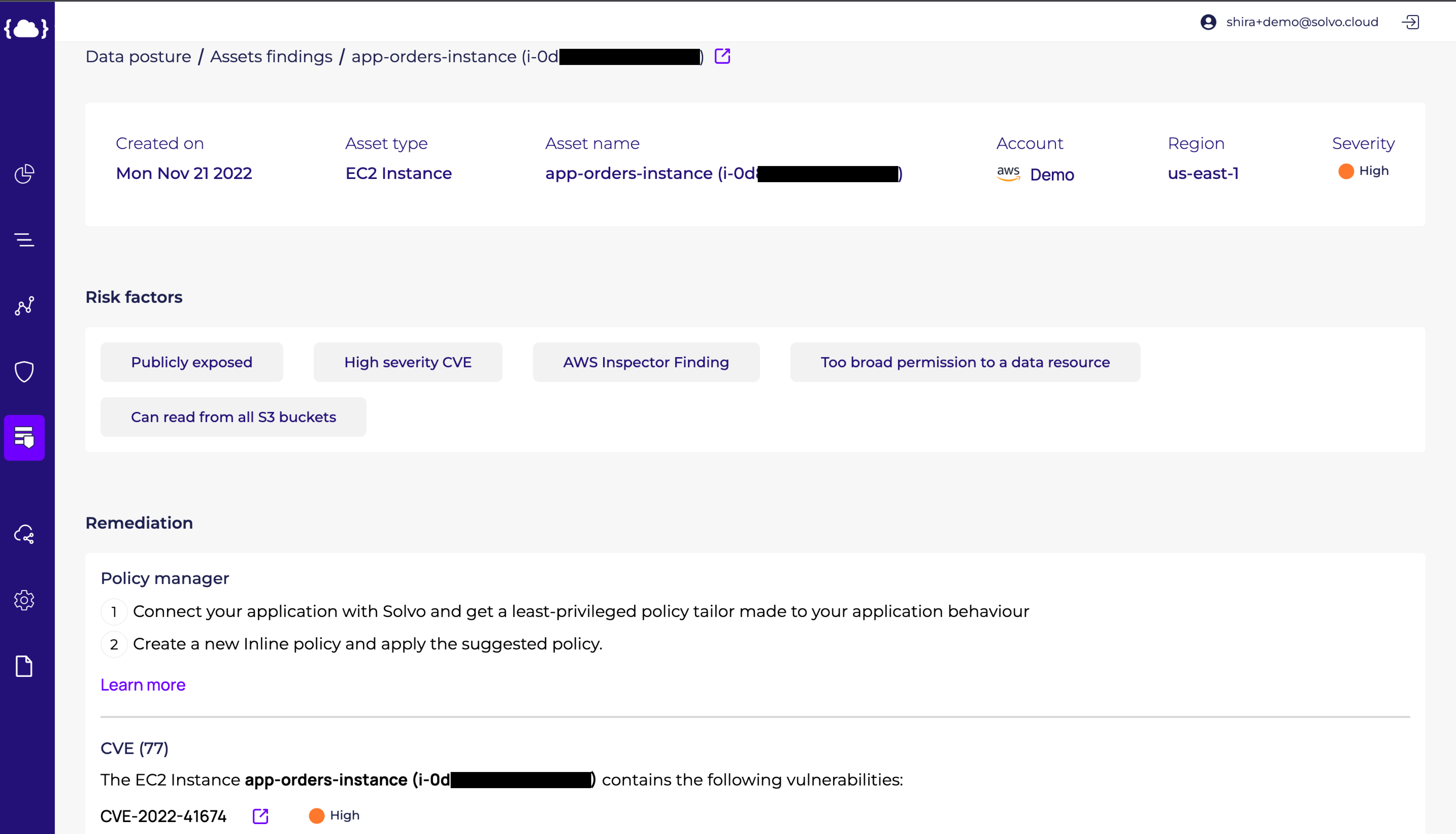
When taking a closer look at one of the findings, we can see the specific risk factors the Solvo algorithm brought into consideration when creating the scoring.
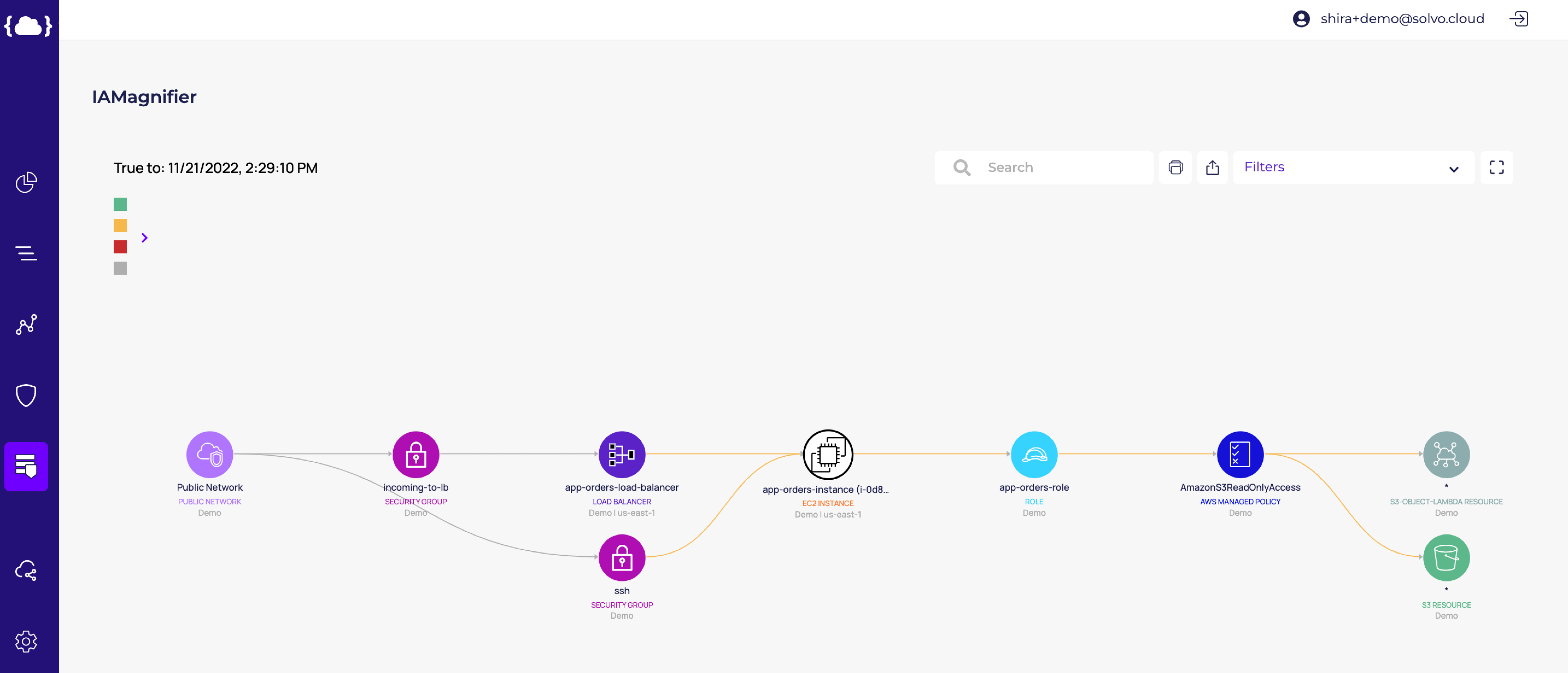
In the finding above we can see an EC2 instance with a risk score of ‘High’. The risk factors that impacted this score are: ‘Too broad permissions to a data resource’, ‘Publicly exposed’, ‘Can read from all S3 Buckets’ and ‘High severity CVE’. If you’re wondering how we get to that, you can see below the permissions graph, generated by the IAMagnifier.
The attack surface starts from the public internet, with specific Security Groups enabling access to the EC2. We then follow the graph toward the left side, and see that this EC2 has a security policy called
“AmazonS3ReadOnlyAccess”, that contains a wildcard and enables access to all the S3 Buckets in the account. This broad access is marked as a wildcard (*) on the right side of the graph. Note that the IAMagnifier marks this access in orange, and lets us know that it is excessive and can be reduced.
It’s easy to see how different components are taking part in the (in)security of the data stored in the cloud. In order to protect this data resource we need to make sure that no other resource or identity is directly or indirectly connected to it and therefore does not pose a threat.
When we want to understand the blast radius, we must understand that a single cloud resource probably has access to dozens of data resources due to the fact that we reuse security permissions, use wildcards, and attach managed policies (managed by AWS or even by the security team).
Thus creating a security policy that is generic to a certain extent and has some degree of freedom. Ideally, we would like to have a custom-made security policy for every cloud component, making it least-privileged.
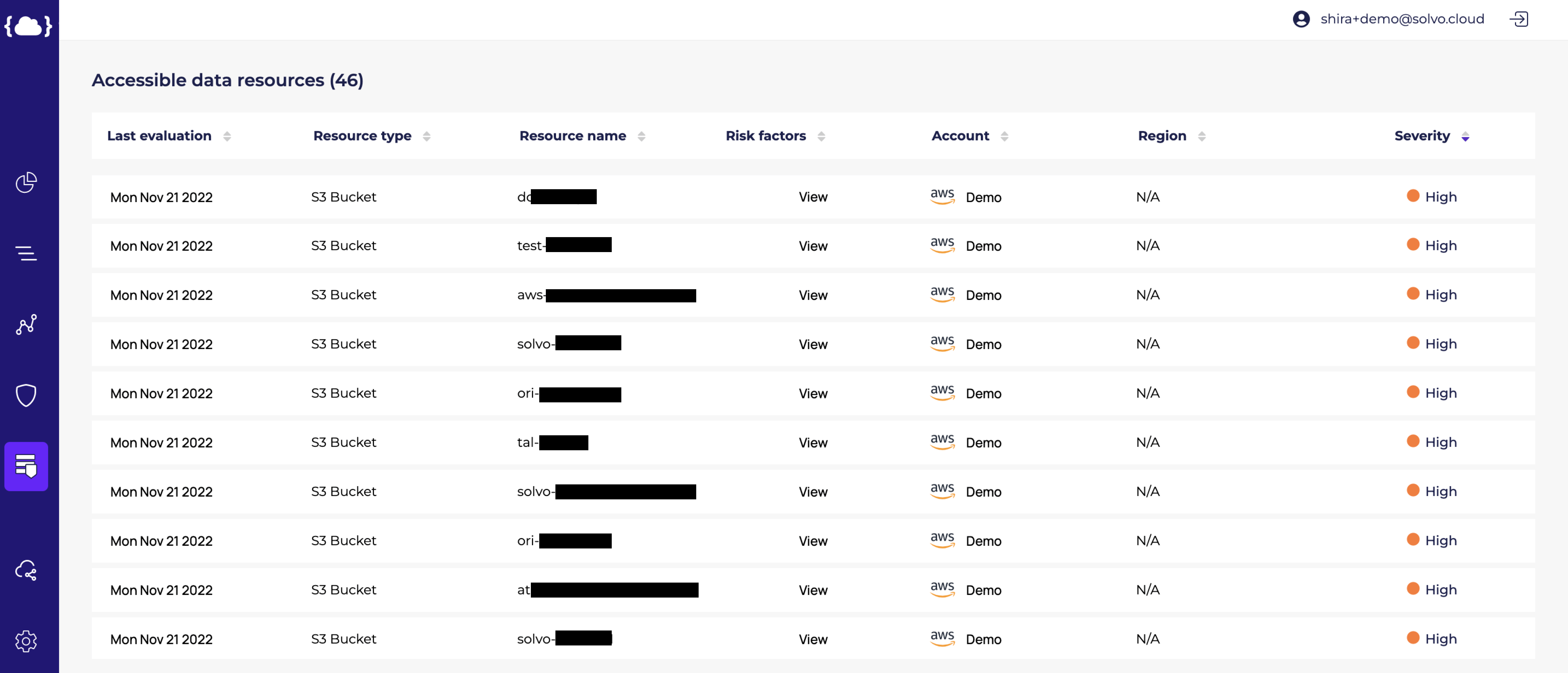
In the image below we can see that the EC2 machine has access to 42 data resources, and Solvo even points out the sensitive data resources (with the orange exclamation mark), because some of your data resources create a different (and higher) kind of risk.
The divine ideal of customized security policies based on the needs of each component is not a dream. Solvo provides it as part of our Policy Manager capability.
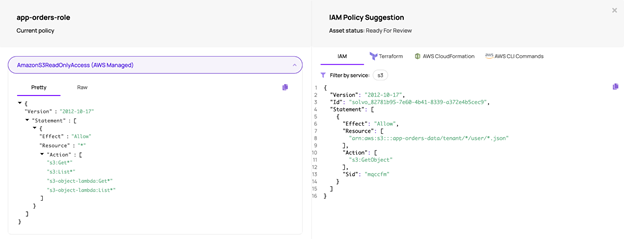
In the example we are going through, we saw an EC2 machine that has read access to S3 using an AWS managed policy. This is the security policy you can see on the left side of the image below.
Using AWS managed security policies is a common practice, but since this security policy is generic, it always contains a high volume of excessive permissions.
In our example, the “AmazonS3ReadOnlyAccess” allows the EC2 to read data from ALL S3 buckets, without any limitation, while based on the application’s needs, this EC2 machine only needs to read data from a specific bucket.
On the right side of the screen we can see Solvo’s suggested IAM policy. The policy was generated after analyzing the application’s behavior and understanding its context.
We can see it generated a least-privileged security policy. This policy allows to perform the “GetObject” action from a specific bucket and even points at the specific partition in the bucket (path), where the relevant objects are.
To complete the process, Solvo helps you to remediate these security findings at scale by integrating with your IM, ticketing, and security orchestration tools, where you can get notifications about new security findings and their correlating remediations. Prevention, detection and remediation were never easier.
To learn more about what YOUR cloud application looks like, its top risks and vulnerabilities, click here and get started!