On January 21, 2021 Ubiquiti Networks, an American technology vendor of cloud Internet of Things (IoT), disclosed that it had suffered a data breach. Ubiqiti sent out emails to its customers asking them to change their passwords and enable 2FA for their accounts.
At the time of the disclosure, the company announced that it had discovered unauthorized access to some of its systems managed by a third-party cloud provider.
It also added it was not aware of any access to any databases that contained user data. After the publication of these materials, Ubiquiti’s share price fell by 20% in just a day, and the company lost $3.9 billion in market capitalization.
Now new information has emerged from the investigation. According to an indictment unsealed by the US Department of Justice (DOJ), a former Ubiquiti developer was arrested and charged with stealing data and trying to extort his employer while pretending to be a whistleblower.
While the DOJ didn’t name Nicolas Sharp’s employer in the press release or the indictment, all the details perfectly align with previous info on the Ubiquiti breach.
What Really Happened at Ubiquiti and Lessons Learned the Security Hack
The indictment reports that Sharp used administrative access to download confidential data, using a VPN to hide his IP address while he pulled from the company’s AWS and GitHub databases.
The investigation found out that it was possible to associate unauthorized downloads with Sharpe, since during the download his connection was interrupted several times, which disrupted the VPN connection and revealed his IP address.
Sharp is alleged to have downloaded an admin key which gave him “access to other credentials within Company-1’s infrastructure” from Ubiquiti’s AWS servers.
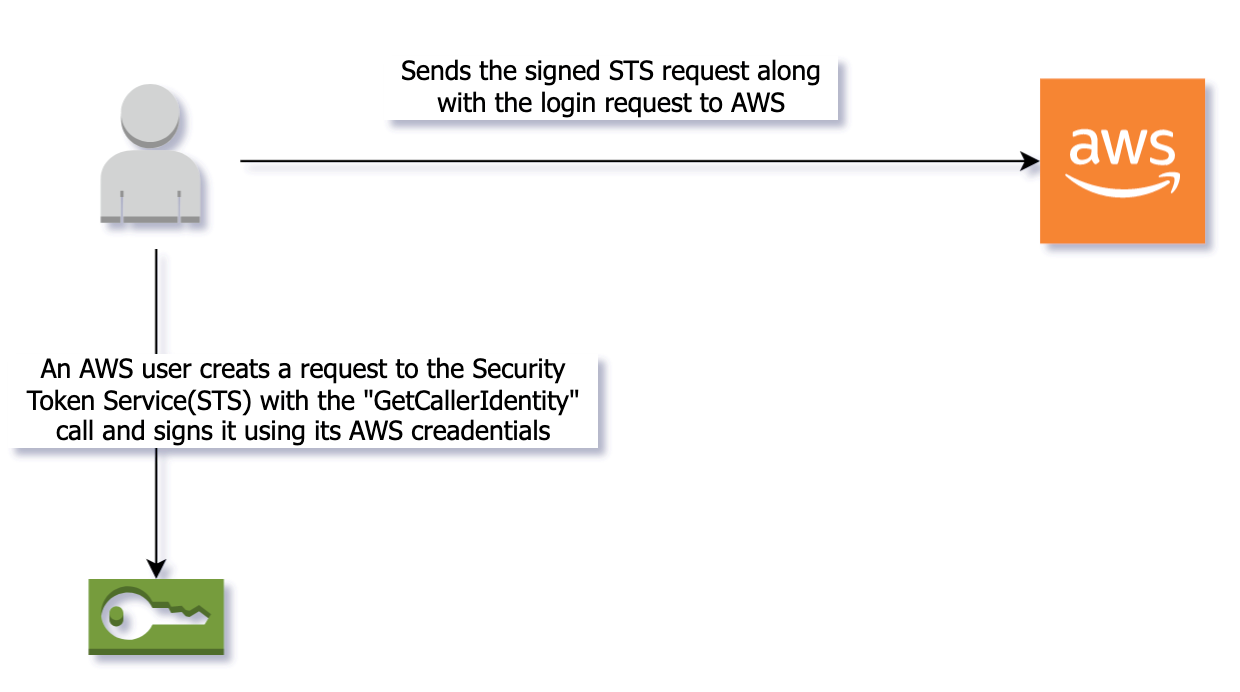
Later, that same key was used to make the AWS API call GetCallerIdentity from an IP address linked to VPN provider Surfshark, to which Sharp was a subscriber.
The AWS API call GetCallerIdentity returns the account and IAM principal (IAM user or assumed role) of the credentials used to call it. “No permissions are required to perform this operation.
If an administrator adds a policy to your IAM user or role that explicitly denies access to the sts:GetCallerIdentity action, you can still perform this operation.
Permissions are not required because the same information is returned when an IAM user or role is denied access.” IAM User Guide.
However, you can monitor it as an abnormal behavior. For example, an attacker may attempt to verify their current identity with the credentials they hold.
This could both be to verify that the credentials they hold are valid, and to get more information on their current identity for reconnaissance purposes.
According to the prosecution, he is alleged to have set AWS logs to a one day retention policy, effectively masking his presence.
For this reason the AWS recommendation is to centralize your CloudTrail logs in a dedicated restricted AWS account. This prevents an attacker or insider from disturbing them.
Unfortunately, it’s not possible to prevent this issue completely. On the bright side, with Solvo you can be sure that you are doing everything in your power to prevent this from happening to you by:
-
- Restricting permissions to services that should be editable only by specifics.
- Keep your permissions up to date with the usage of the proper identity and checks for behavior anomalies.
- Restrict and monitor sensitive actions on crucial changes of your cloud properties. For example, monitor for unexpected usage of your AWS access keys.
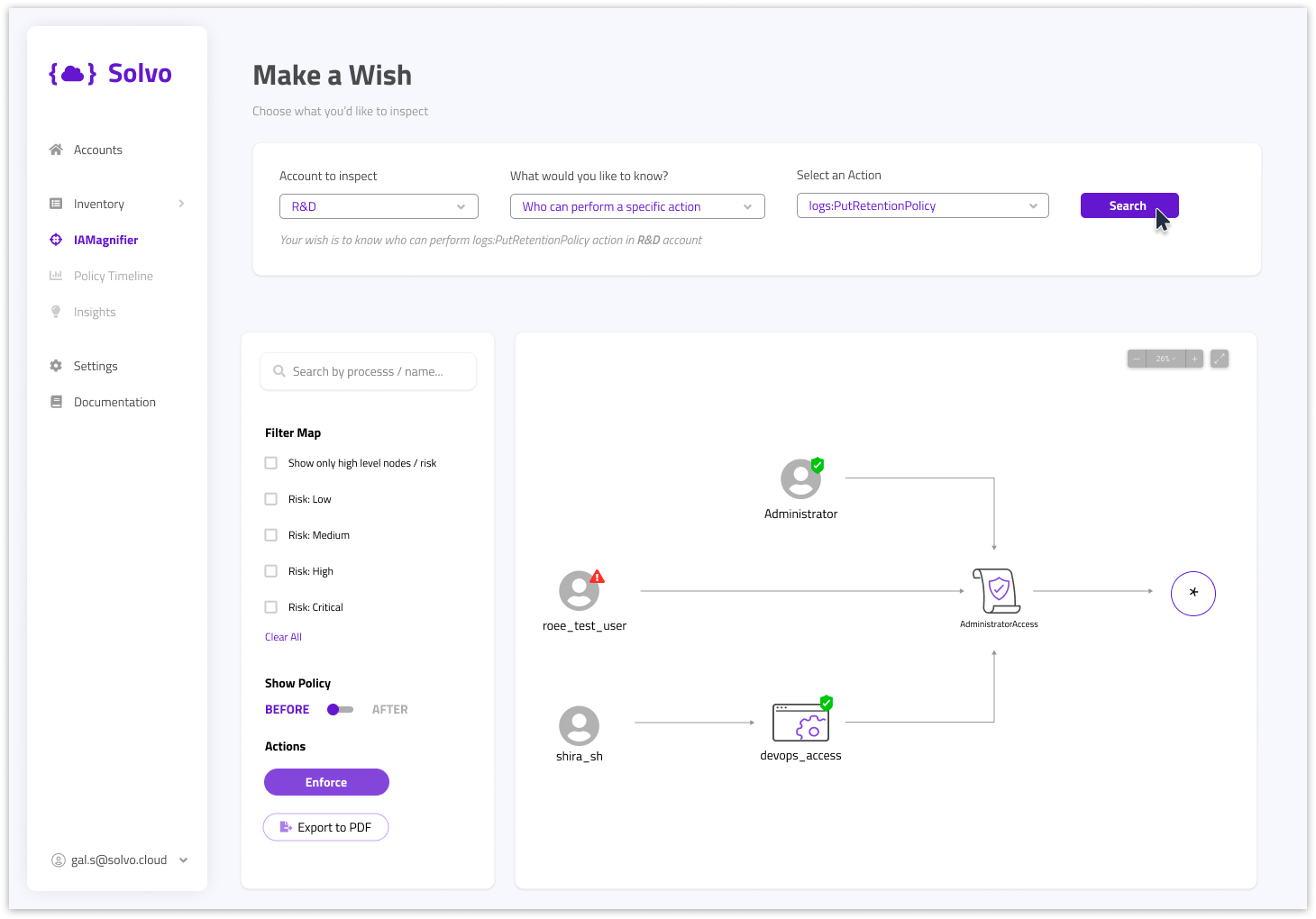
As seen in the image below, Solvo can be used to check who is allowed to make changes to your retention policy.
This way, you can easily discover over-privileged or misconfigured entitlements and make the necessary adjustments as recommended by Solvo.
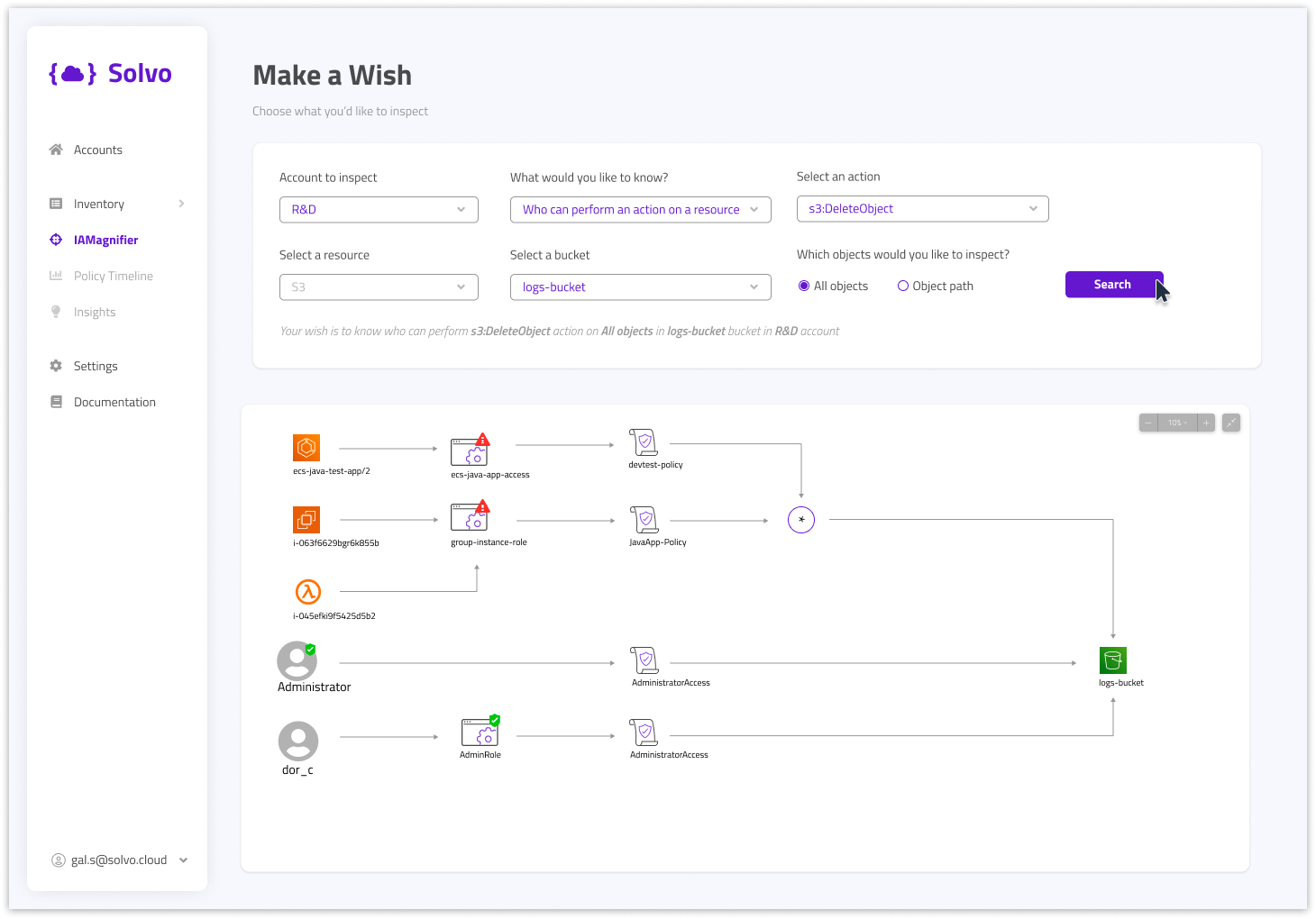
You can ensure the security of your logs by checking not just your policy retention but also whether your logs bucket is fully secure and restricted.
With Solvo’s IAMagnifier, security and DevOps engineers in your organization can easily understand the misconfigurations they currently have, monitor changes in your infrastructure, search for sensitive business processes and set rules for any violation in your permissions boundary.
If you would like to learn more on how Solvo ensures cloud security, reach out to our team for an IAMagnifier demo request and explore all the capabilities of your Solvo solution.
We are ready to lead you to the future of secure cloud operations.