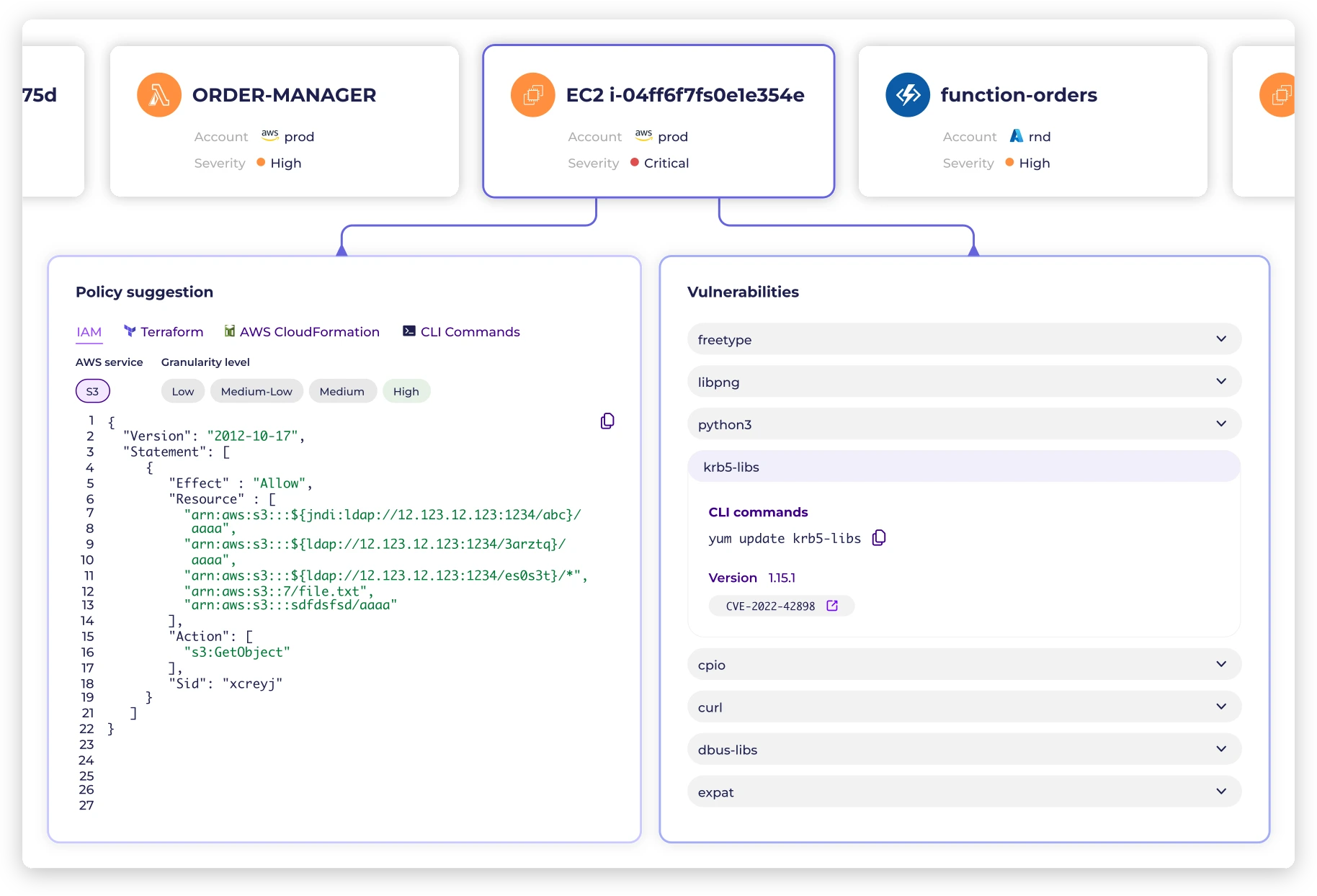
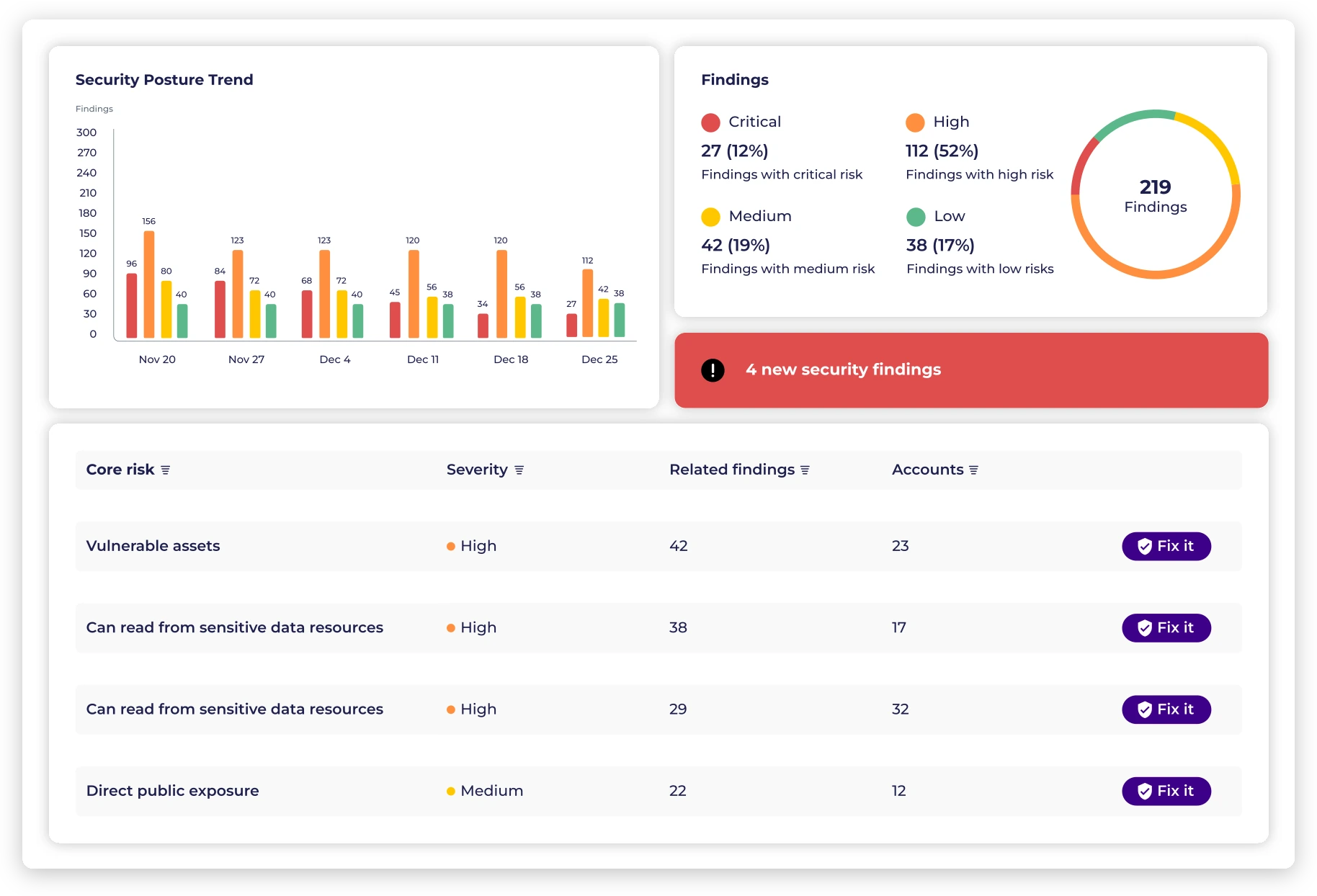
Monitor, identify, prioritize and automatically remediate vulnerabilities and misconfigurations based on contextual, dynamic risk factors.
Leverage real-time application and user behavior analysis, and sensitive data discovery to continuous assess risk, and automate the creation and enforcement of least-privileged cloud infrastructure access policies and entitlements.
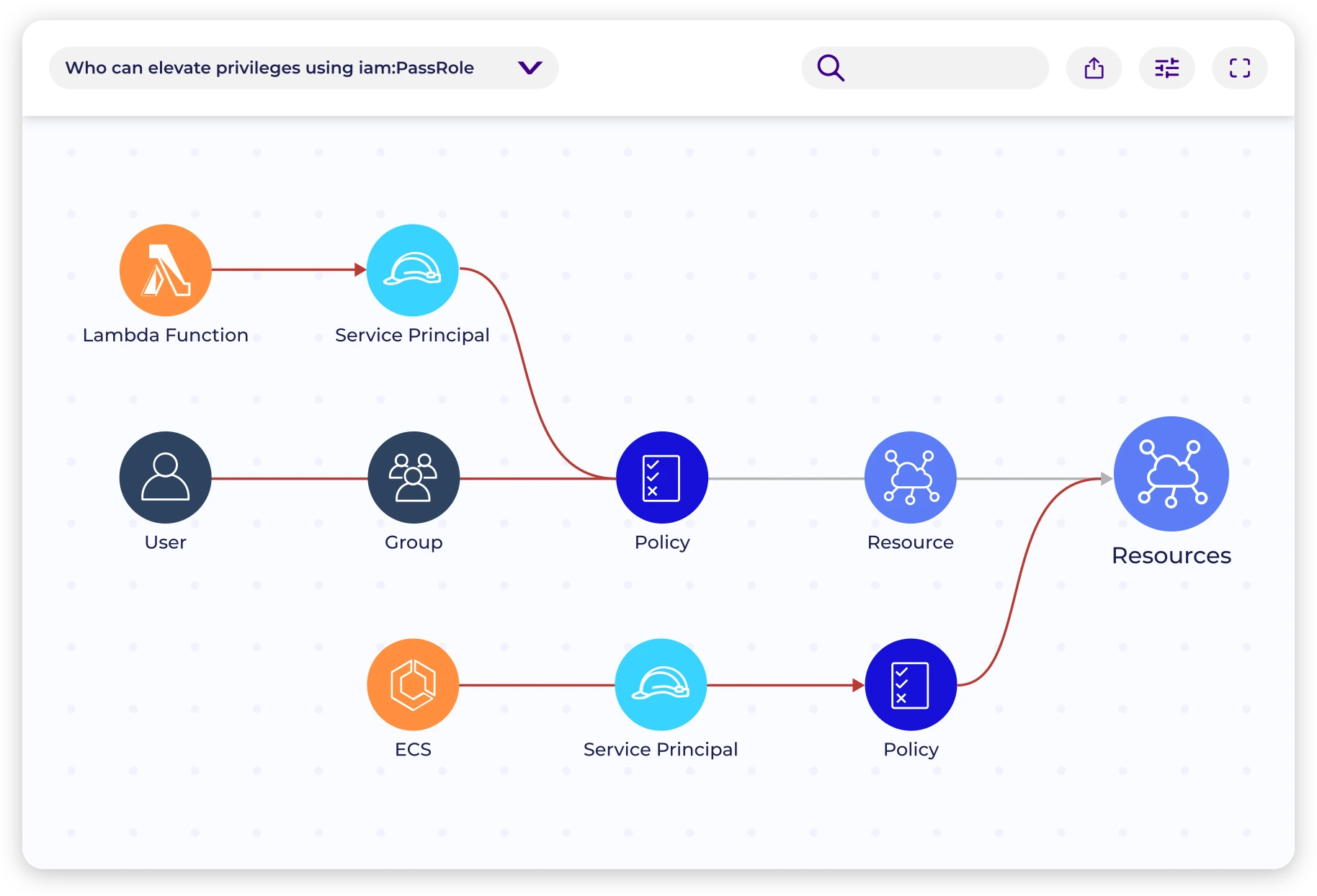
Continuously map human and machine identities and their permissions.
Identify and prioritize cloud access risks based on context.
Create customized, automatically updated least privileged access policies.
Or let us show you around with a demo