Driven by the pressure to rapidly scale up their infrastructure and adapt to changing needs, healthcare organizations worldwide have embraced public cloud services that offer the flexibility, scalability, and agility required to quickly deploy and manage critical healthcare applications. Throughout the COVID-19 pandemic, public cloud services have been extensively used by healthcare companies to support applications such as telemedicine, remote monitoring, and data analytics for tracking the spread of the virus. In addition, these public cloud services have been instrumental in facilitating remote work and collaboration among staff.
The pandemic generated an unprecedented amount of healthcare data, ranging from patient records to epidemiological data. The scalable storage offered by public cloud providers enabled healthcare organizations to effectively store, process, and analyze unprecedented amounts of sensitive data that can be accessed from anywhere. However, this shift has also introduced new security challenges that must be addressed to ensure that critical data and workloads remain secure and accessible only to authorized personnel.
While data breaches and cyberattacks are harmful in any industry, the healthcare sector is a prime target for cyberattacks due to the value and sensitivity of the data it holds, including personally identifiable information (PII), patient records, medical history, and financial data. This sensitive data can be used by attackers to carry out malicious activities, including identity theft, financial fraud, phishing, ransomware attacks, credential stuffing, and more.
An analysis of data breaches recorded on the Privacy Rights Clearinghouse database in the U.S showed that 76.59% of all recorded data breaches were in the healthcare sector. This implies the healthcare sector recorded three times as many data breaches as the education, finance, retail, and government sectors combined.
According to data published by the Department of Health and Human Services’ Office for Civil Rights, and The HIPAA Journal, between 2009 and 2022, 5,150 healthcare data breaches of 500 or more records were reported to the HHS’ Office for Civil Rights (OCR). Those breaches resulted in the exposure or impermissible disclosure of 382,262,109 healthcare records.
Overall, the data shows that healthcare data breaches are on the rise. In 2018, breaches of 500 or more records were being reported at a rate of around 1 per day. 5 years later, this rate has more than doubled. In 2022, an average of 1.94 healthcare data breaches of 500 or more records were reported each day.
In addition to the potential damage to their operations, a cloud data breach may expose healthcare companies to violations of data privacy regulations such as HIPAA, as well as hefty financial penalties. For example, in 2018, health insurance provider Elevance Health (FKA Anthem Inc.) paid $16 million to resolve potential HIPAA violations that were discovered by the OCR as part of the investigation of its 78.8 million record data breach in 2015.
The rapid adoption of cloud technologies, driven by urgency, may have led to potential security oversights. Moving data and workloads to the cloud expands the attack surface as it increases the potential points of entry for cyber threats. Moreover, cloud environments are highly configurable, and human error such as misconfigured access controls or improperly secured storage buckets can lead to data breaches. Healthcare organizations may lack the necessary expertise or resources to properly configure and monitor their cloud environments, making them vulnerable to
these types of errors.
Healthcare organizations may also be at risk of failing to comply with data sovereignty laws, which dictate where certain types of data can be stored or transferred. Public cloud services may have data centers located in different jurisdictions, which can introduce challenges related to compliance and legal obligations.
To address these challenges, healthcare organizations must work closely with cloud service providers. Although the leading public cloud providers offer strong security features, customers are responsible for safeguarding their own data and applications in accordance with the shared responsibility model. Nevertheless, establishing suitable access policies and controls to ensure the protection of sensitive data poses a significant challenge – and particularly for healthcare organizations.
One of the main factors that impedes healthcare organizations from implementing effective least privilege policies across their cloud infrastructure is that healthcare systems are often implemented with broad access permissions. This enables physicians to promptly retrieve necessary data when needed.
Let’s consider a scenario in which a surgeon is performing a complex and time-sensitive procedure in the operating room. During the operation, the surgeon realizes they require immediate access to the patient’s medical imaging scans for real-time guidance. However, if access to the imaging system is restricted or requires additional approval, it could delay the surgery and compromise the patient’s safety.
In such critical moments, quick and seamless access to the necessary data is crucial to make informed decisions and ensure the best possible outcome for the patient. However, without proper protection, malicious actors can exploit these extensive access rights to gain unauthorized entry and even assume control of an entire healthcare system.
Furthermore, healthcare organizations typically have a wide range of user roles, including healthcare providers, administrative staff, IT personnel, and third-party vendors. Each role requires different levels of access to the cloud infrastructure and sensitive patient data. Defining and enforcing least privileged access policies for these diverse user roles can be complex and time-consuming.
Overcoming these challenges requires continuous assessment of access controls to ensure the least privileged access principle is effectively implemented and maintained. However, given the vast size and complexity of cloud infrastructures, and their dynamic nature, it’s becoming increasingly challenging to monitor changes, assess risks, and establish access policies and permissions accordingly.
This repetitive process becomes even more demanding when managing multi-cloud deployments. In this situation, it’s nearly inevitable that errors will occur – such as misconfigured entitlements, unused privileged accounts, or excessively permissive permissions that go undetected for too long – thus creating vulnerabilities that attackers actively seek to exploit.
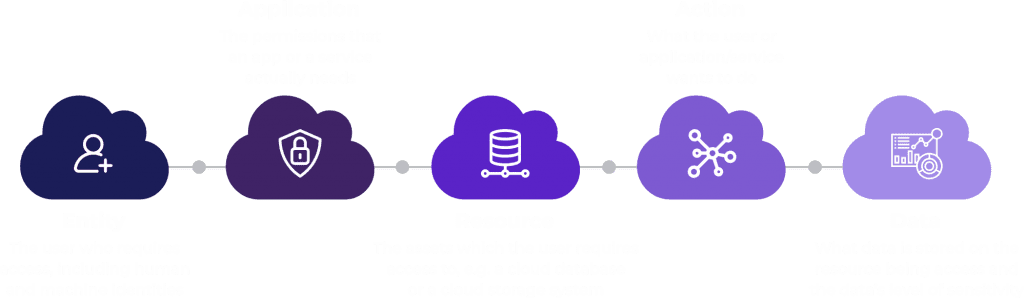
By gaining visibility and constantly analyzing configurations, relationships, and activities across these dimensions, retailers can identify and mitigate vulnerabilities in a timely manner.
They can prioritize risk and automatically apply the right policies and entitlements on an ongoing basis while reducing the operational burden on security teams and developers.
Solvo takes a different approach to cloud security, enabling healthcare companies to automatically uncover, prioritize, mitigate and remediate cloud infrastructure access risks. Using multi-dimensional, contextual monitoring and analysis of infrastructure resources, applications and user behavior, and the data associated with them, Solvo facilitates the implementation of adaptive least privilege access policies and controls at scale.
Solvo automatically creates customized, constantly-updated least privilege access policies based on the level of risk associated with the entities and data in the cloud. This way, it helps various stakeholders to identify and prioritize risks, simplify compliance, and proactively mitigate cloud misconfigurations and vulnerabilities while facilitating collaboration between security, DevOps and engineering teams.
Solvo’s unique platform gets to work right away in three distinct stages:
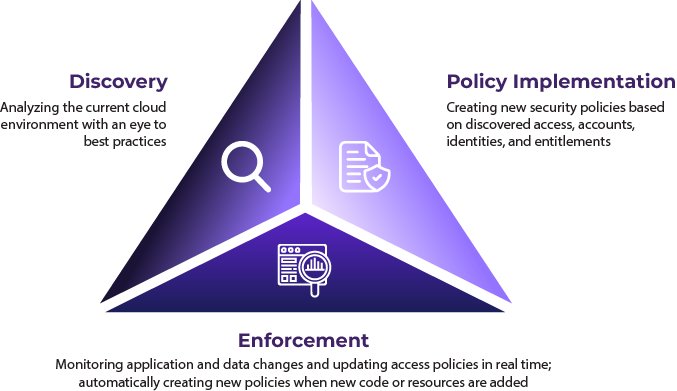
Modern healthcare services rely on public cloud infrastructure to streamline complex processes. The critical nature of healthcare services requires the assigning of broad access rights to various users so they can log in and retrieve any required patient information, often in life-saving situations. Nevertheless, broad access rights also open the door for malicious individuals to exploit their access for illicit or improper motives.
The consequences of such incidents are substantial. According to the annual Cost of a Data Breach Report, conducted by Ponemon Institute and sponsored and analyzed by IBM Security, healthcare breaches cost the most by far, at $9.23 million per incident.
To avoid the high costs of healthcare breaches, healthcare organizations that move critical workloads to the cloud require a proactive and adaptive approach. By implementing a cloud security solution such as Solvo, healthcare organizations can safeguard sensitive data stored in the cloud while maintaining a high level of accessibility for authorized personnel.
Discover and address cloud risks effectively and empower your security team with the autonomy they need.
Or explore on your own time with a free trial