New Year’s resolutions aren’t the only thing you should be preparing for this time of year. January 1st, 2023, CCPA will come into effect. The CCPA (California Consumer Privacy Act) is, in a way, California’s version of the EU’s GDPR regulation with the purpose of protecting PII / customer data.
While there are some differences between the two regulations (for example, CCPA protects ‘consumers’ while GDPR protects ‘data subjects’), their goals are similar – protecting the data that could identify people and holding businesses accountable when storing it or using it.
After some delays, CCPA is almost here, so you better start preparing. Even if your business is not located in California, but you’re doing business there, CCPA applies. If you own, are owned by, or share branding with a company that the CCPA applies for, it might be applicable to you too.
For your business to comply with CCPA (or other similar regulations), you should have a good understanding of the type of data that you store, how it is stored, and who has access to it – should a customer ask to know more about it or ask to delete it.
While controlling data in large organizations is known to be a tough task, for organizations in the cloud it gets a little tougher. Usually, because there are more people with access to the infrastructure and the loss of control over some workflows. For example, you could find dumps of your data in non-production environments because developers ran some tests and left them there.
The security team doesn’t know it’s there, and therefore cannot guarantee that it’s well protected. If you don’t know it you can’t protect it and therefore might violate the regulatory requirements.
Some people believe that if they are using the public cloud (AWS / Azure / GCP or others) they are protected and compliant, but this is far from the truth. By now you’ve probably heard about the Shared Responsibility Model.
It means that there are some things the cloud vendors are responsible for, like the hardware and the software that is used to run it. But you are responsible for how to use it and what it is used for.
So configurations, encryption and even patching the OS are some of your responsibilities. The basic principles of being compliant in the cloud are not very different from the on-prem. We just need to make some adjustments as to how we become and remain compliant in the cloud.
Here’s a list of a few things you should check and ask, to feel more confident when CCPA comes into effect:
1. Where are my data resources? Where is my data stored?
“In the cloud” is not the correct answer. You’re probably managing several cloud accounts, with different users having access to various accounts, some are production while some are not.
So where did you say the data was? Most cloud users don’t even know how many blob storage components they have.
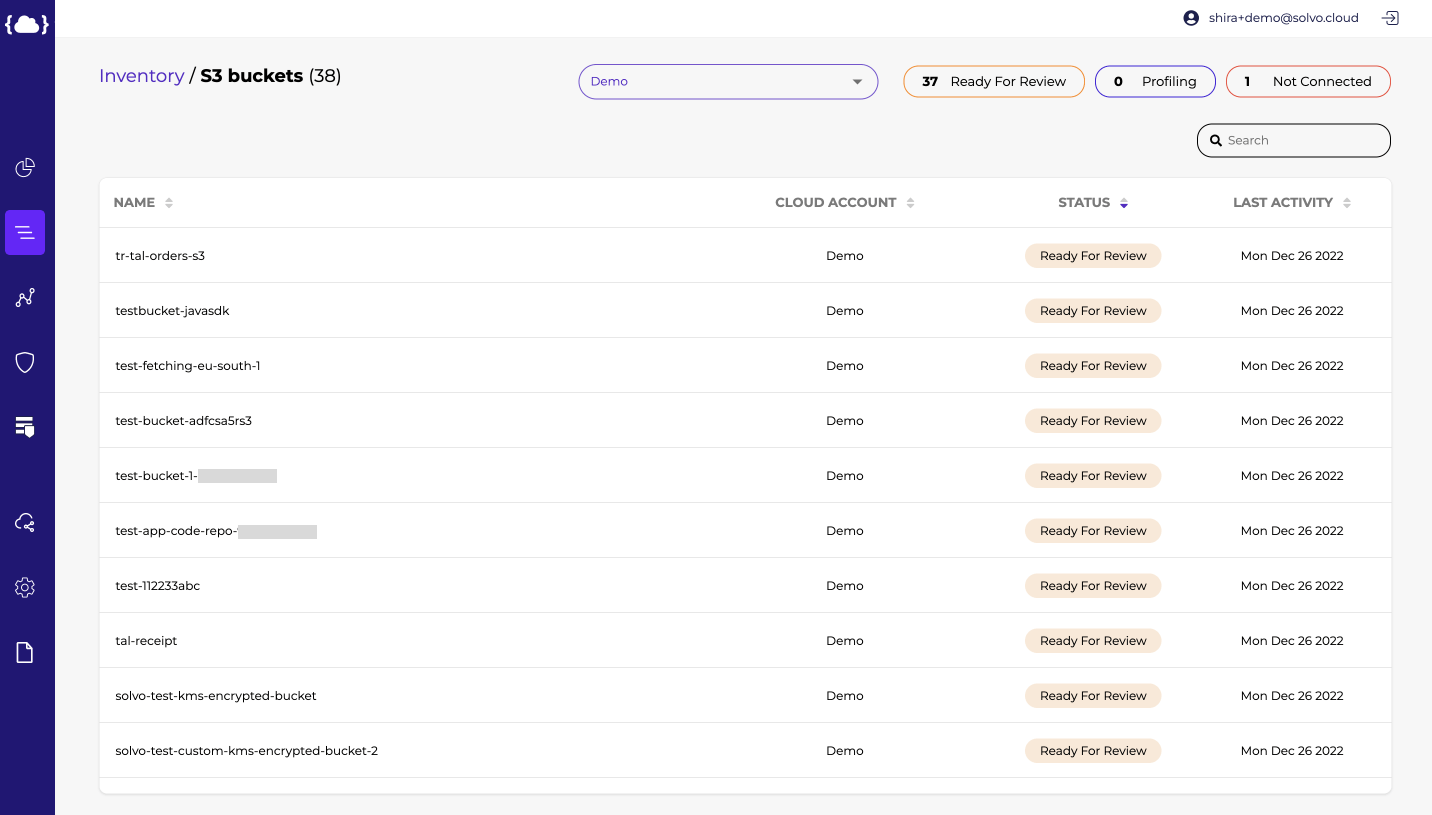
To have a good answer to this question, you need to have an understanding and control of your inventory. Data resources included.
How Solvo helps:
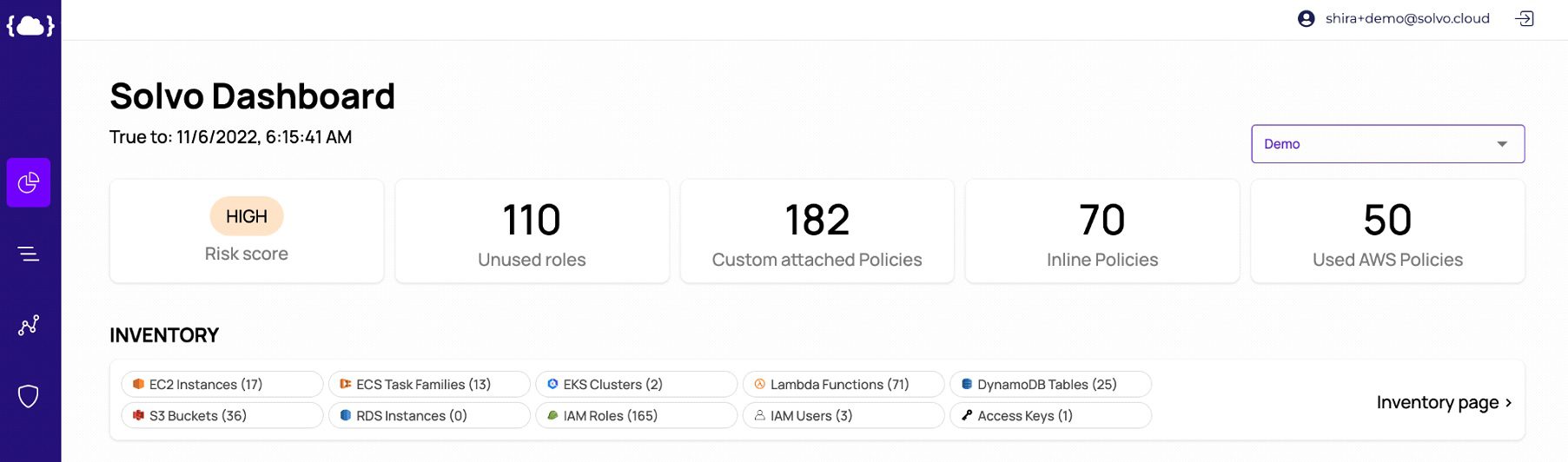
In the Solvo console, you can get a list of your data resources by type and per account. This way you can control any data resource one of your team members spun up.
If you want a general overview of the number of resources you own in the cloud and data resources being a part of that, you can check out Solvo’s dashboard and look at the inventory section.
2. How is this data protected? Is it encrypted?
There are several best practices for data protection. Encryption is probably the most basic and most useful one. If you have a data resource, use encryption. There is no reason not to do it since this technology is practically baked into any data service you wish to use.
Often R&D teams think “it’s just a tiny dump” or “I’ll just test with this data set and then delete it” but they fail to realize and understand the sensitivity of the data at hand. Due to this, you must enforce the encryption policy at all times. In the first section, you discovered your data resources, and now you need to make sure that all of them are encrypted.
How Solvo helps:
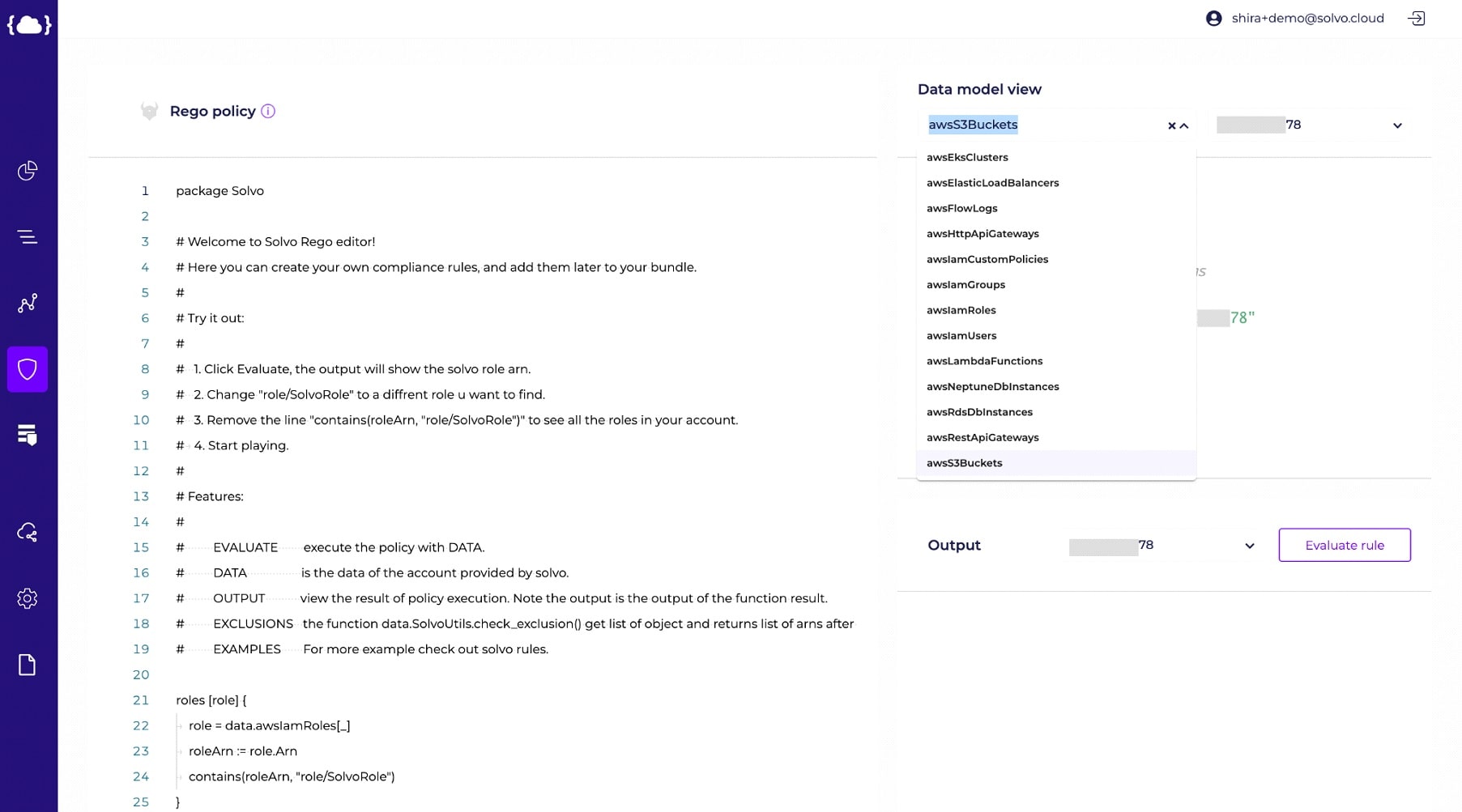
Solvo’s Compliance Manager is a powerful tool that helps you validate your compliance status for different regulations out of the box, or create your own rules you wish your organization would comply with, using the popular OPA open-source project and their useful Rego language.
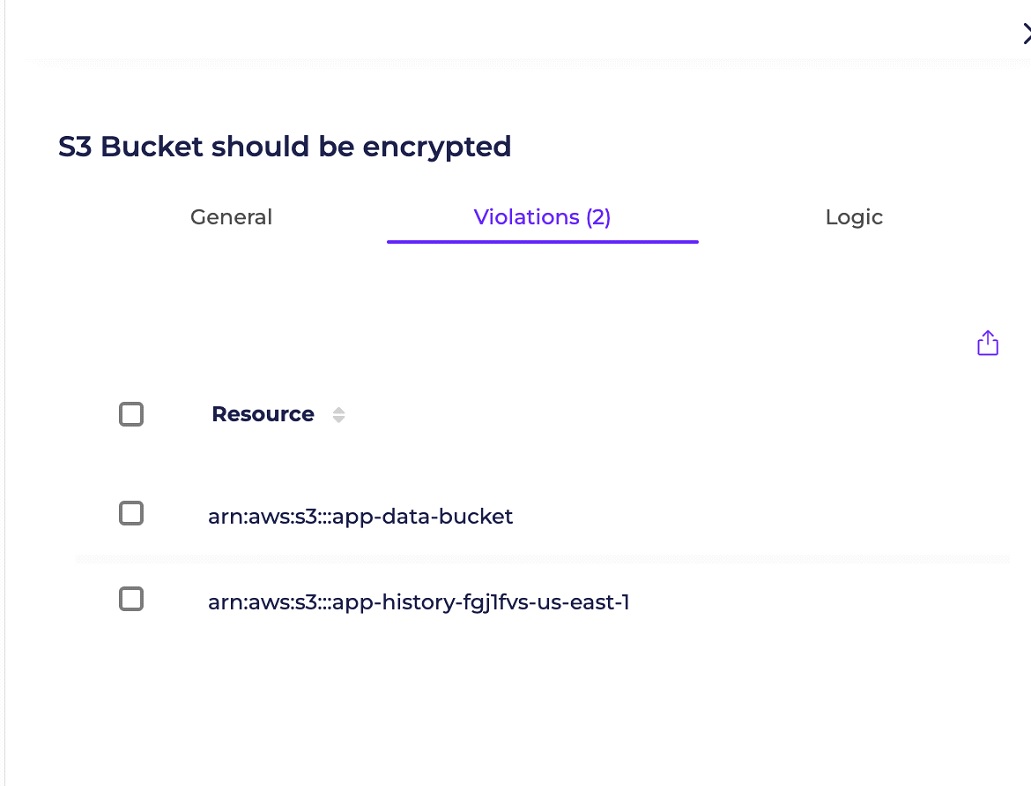
This way it is easy to see which data resources are not encrypted. Even if all your data resources are encrypted at this very moment, we never know what tomorrow will bring – maybe someone will expose an S3 bucket to the internet (by mistake of course), while it contains unencrypted data? The Compliance Manager will notify you of a new violation of the compliance rule that you have enabled.
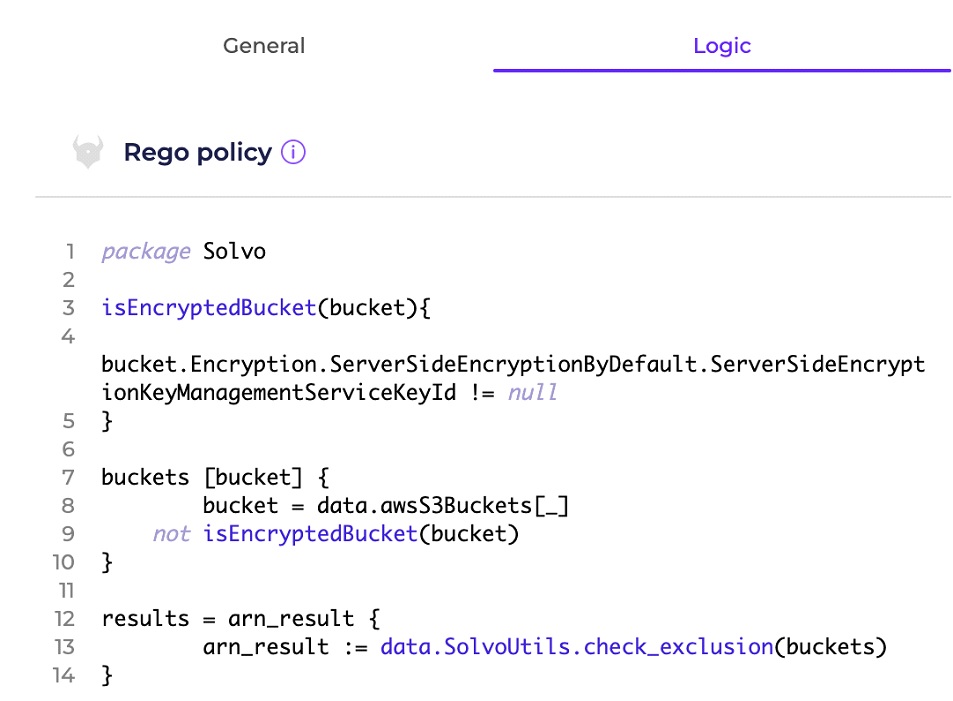
Below is an example of a Rego policy that checks if S3 Buckets are encrypted. By activating it, you will get a list of all unencrypted buckets, and will be notified if new buckets are created without adding encryption. In a similar way, you can create or use out-of-the-box compliance rules easily.
If you’d like to create your own rules, that’s very easy to do using Solvo’s Compliance Manager.
And then track the violations in the Compliance Manager screen, like this:
3. Who has access to this data?
So now you know where your data resources are, and that they are encrypted the right way. Now let’s check who has access to them, and what kind of access they have. By “who” it means you need to check which users have access to the data, and also which other cloud components have access to it.
Other cloud components could be compute resources, but also users and 3rd party’s external cloud accounts. It’s important because malicious activity can be done not only by users directly, but also by users who can trigger other cloud components to run activities for them (like making a lambda function read an entire DB and write it in another DB for which they have access).
Now that you know who has access, you should check what kind of access they have. You probably heard about the least-privileges principle. That means we should grant only the necessary privileges to the ones who need them.
Therefore, if you have a container that only needs to read an item out of a specific DynamoDB, there is no need to grant it full read/write permission, just let them do what they need to do.
How Solvo helps?
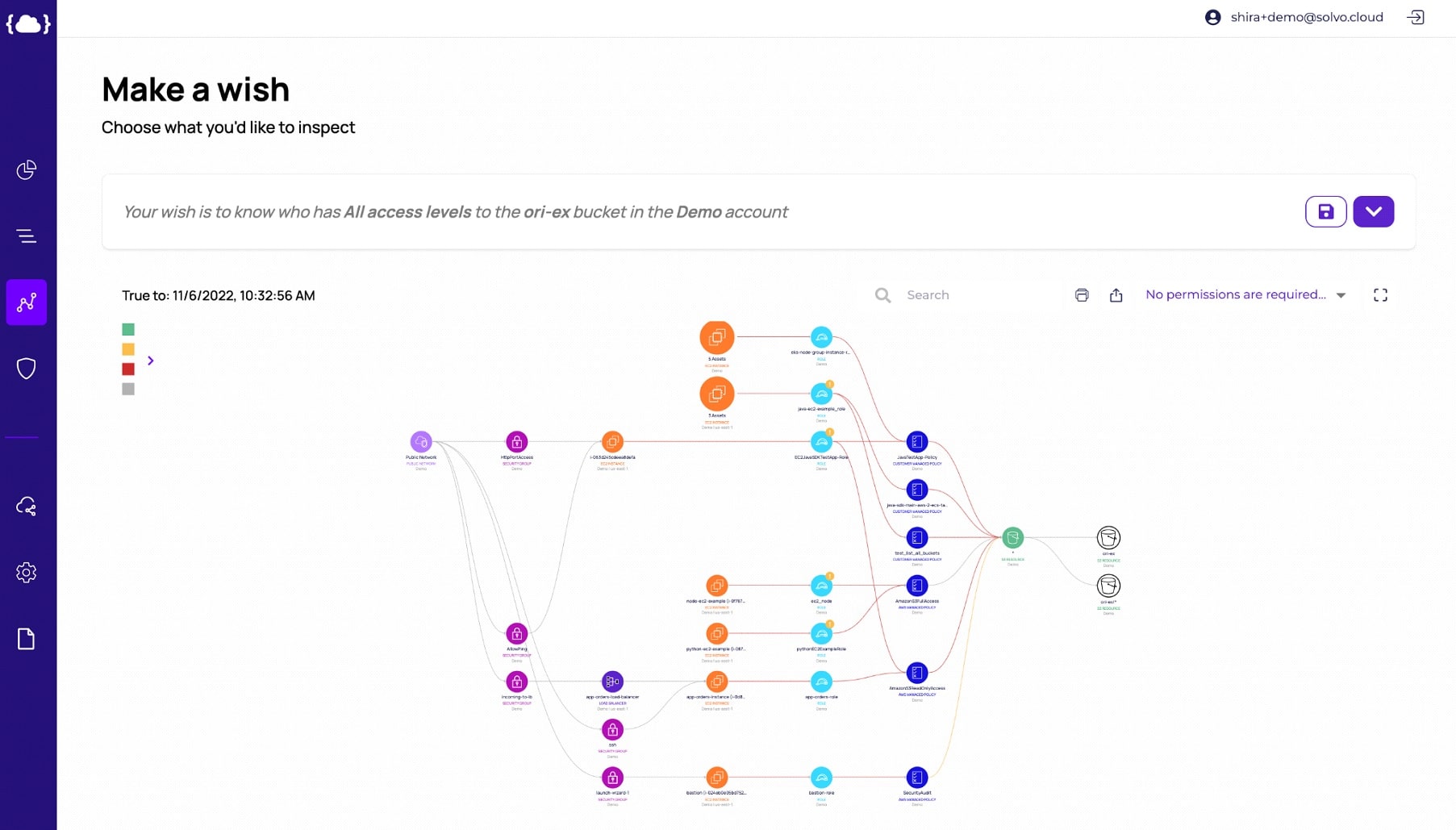
To better understand who has access to your data, and what kind of access they have, Solvo created the IAMagnifier. This powerful tool shows you a graph of your inventory, including the permission model, that’s enabling access of any kind.
The IAMagnifier is turning the complicated permission model into a clear and actionable graph. Using the IAMagnifier you can inspect your crown jewels, create notifications, should a new permission be added, and be confident that once you’ve reached compliance things will remain this way.
The IAMagnifier shows you not only the existing permission model but also which permissions are excessive. Having excessive permissions hurts your compliance and is making your application exploitable. With the IAMagnifier you can safely remove excessive permissions, as they are unnecessary for the functionality of the application and could be used for malicious purposes.
4. What should be the right-sized permissions?
Cloud applications are dynamic and change frequently. This means that to remain least-privileged, the security permissions should change and adapt to the application in the same cadence.
You need to verify that your permissions are just what the application needs. Having too few permissions would cause denied actions, and having too many permissions create an attack surface.
So check the IAM policies, who has them, and who uses them, remove unused roles and look for “surprises” in your IaC files. Try not to use wildcards, there are rarely any real use cases to do that. Also, try not to use the security policies created by the cloud vendors since they are generic and very broad.
How Solvo helps?
Solvo can right-size permissions for you, from the data resource standpoint (S3 resource based policy for example) and also from the compute resource standpoint (Identity IAM policy for your Lambda function’s role for example).
This happens automatically and continuously. Should anything change in the application that would require a change in the security policy, Solvo’s Policy Manager will detect it and send a suggested IAM policy for your approval.
Below we have two examples for the two policy types mentioned:
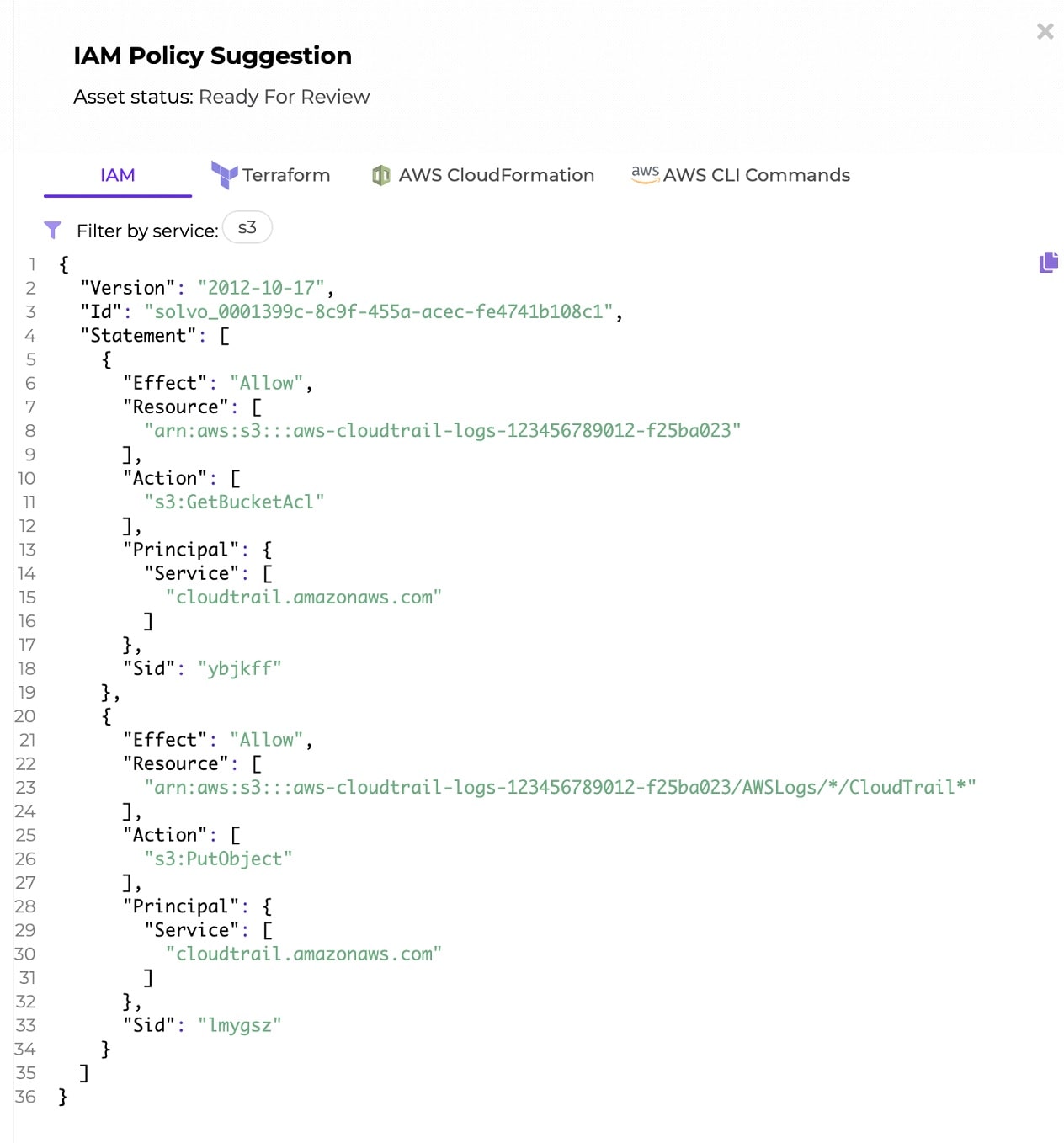
S3 resource based policy for a bucket (in this case, a bucket that stores CloudTrail logs), making sure only the necessary actions can be executed.
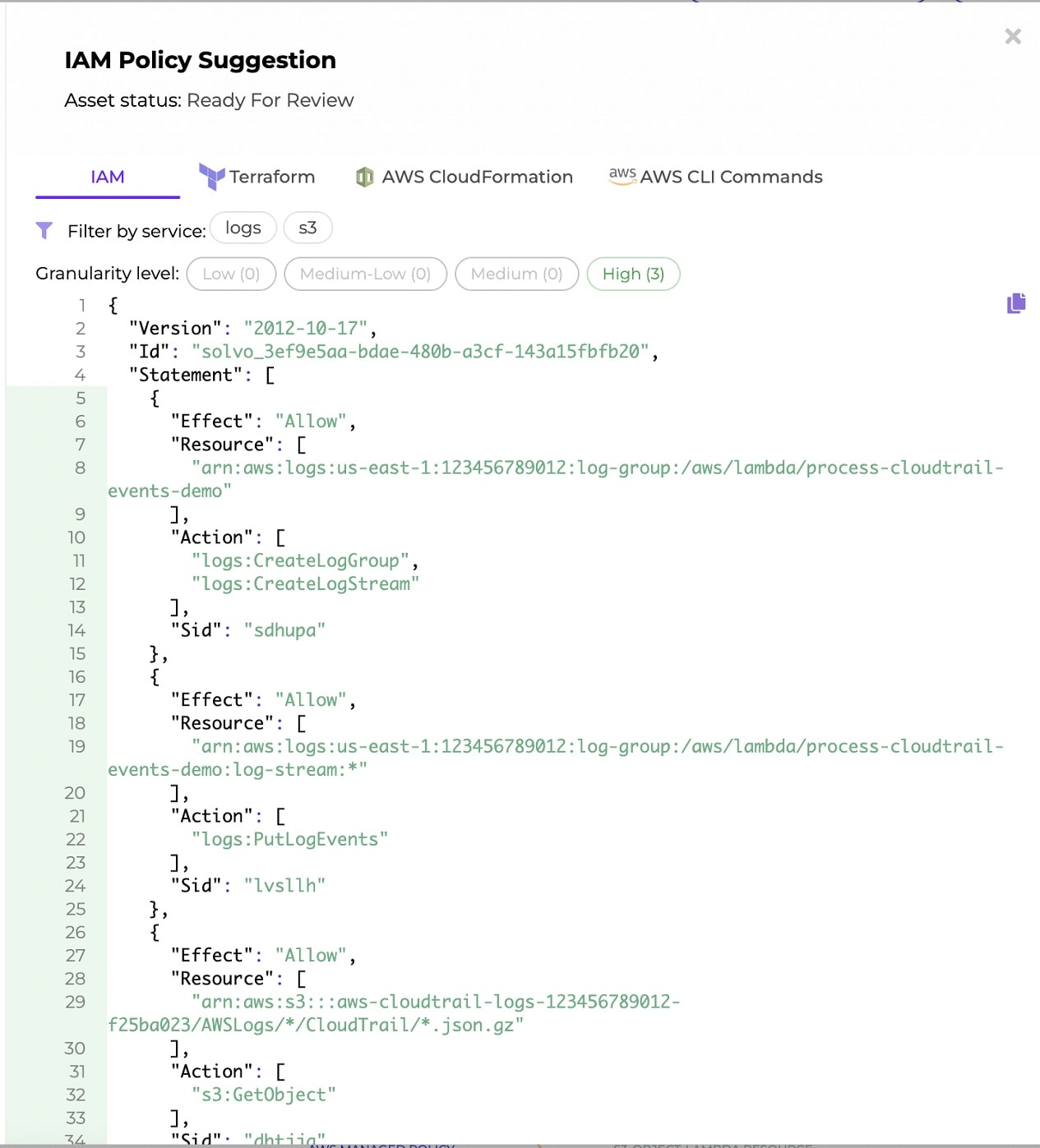
Below is an example of an IAM policy of a lambda function that needs to read out of the CloudTrail S3 Bucket. Solvo generated it automatically and based on its specific applicative needs. The access is granular and gives the specific actions the Lambda needs to perform, on the specific resources.
5. What’s changed? Do we have any drifts?
Once you successfully pass the security audit you can forget about data security until next year. NOT! You actually need to maintain this great accomplishment until next year’s audit, and also in general because it’s the right thing to do.
Therefore you need to make sure that you are aware of any drifts from the existing status, either in existing cloud assets or in new ones that will be spun. You should also make sure to fix vulnerable and misconfigured cloud assets within a reasonable period of time. The longer it takes, the bigger the chances are that someone will exploit the situation, and you will have to pay $$$ in fines.
How Solvo helps?
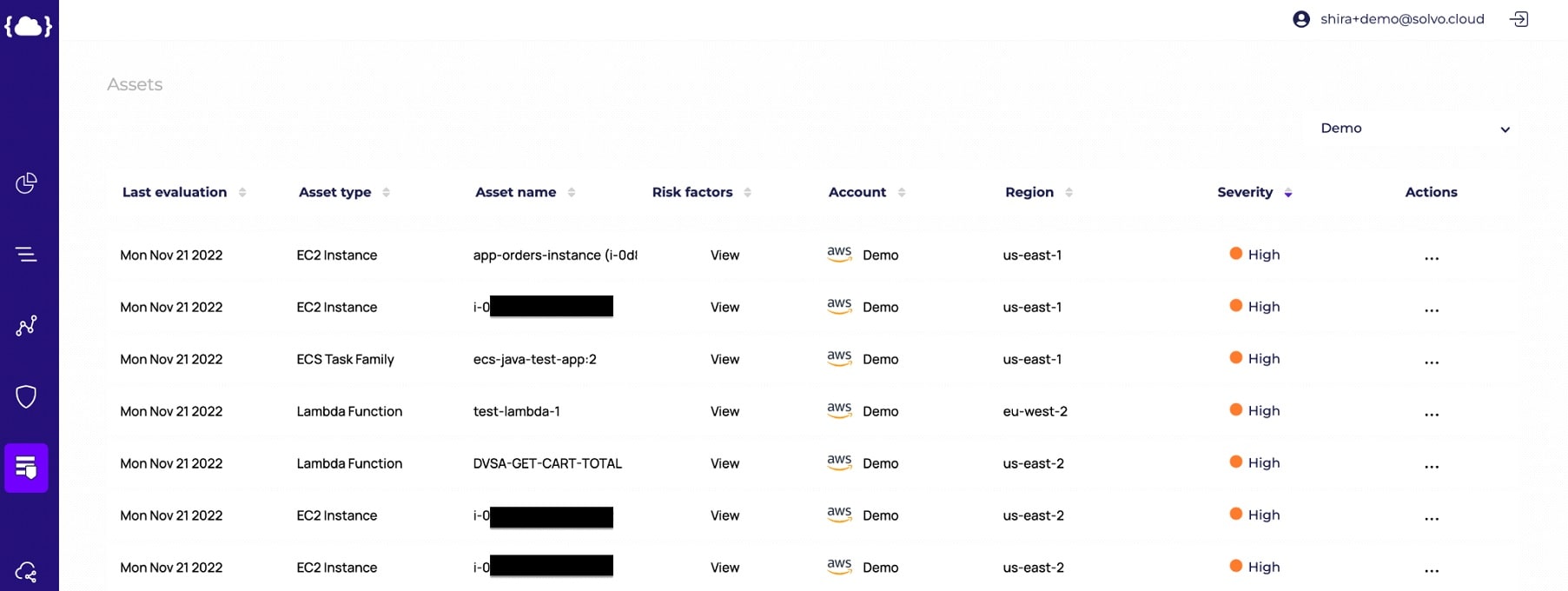
The new Data Posture Manager is here to help you. This feature shows a prioritized list of your security, risk, and compliance findings. It will point you to where your attention is needed the most, and provide you with actionable insights and remediation options for the specific finding.
The prioritization is based on our dynamic risk scoring algorithm and brings into consideration misconfigurations, vulnerabilities, connectivity to other cloud components (and their vulnerabilities), paths to sensitive data resources and business impact. Your cloud application is dynamic, and so should the prioritization you’re working by.
When combining Solvo’s Compliance Manager with the Policy Manager you get a powerful capability to detect drifts from current status or best practice, along with a clear remediation you can easily enforce as part of your CI/CD process or change management process.
Consume Solvo’s findings and least-privilege security policies through the ticketing system, IM, or other workflow management system of your choice.
Below is a prioritized list of findings, all related to the data resources in the account and have an impact on our crown-jewels, even if not stored there directly. Always consider the blast radius and how attackers can make their way from the internet to your data.
Prepare yourself for the CCPA today! See your environment through the IAMagnifier, understand your risks with the Data Posture Manager, and fix them with the Policy Manager.
Start a free trial, check us out on the AWS marketplace or watch our CCPR webinar to learn more.