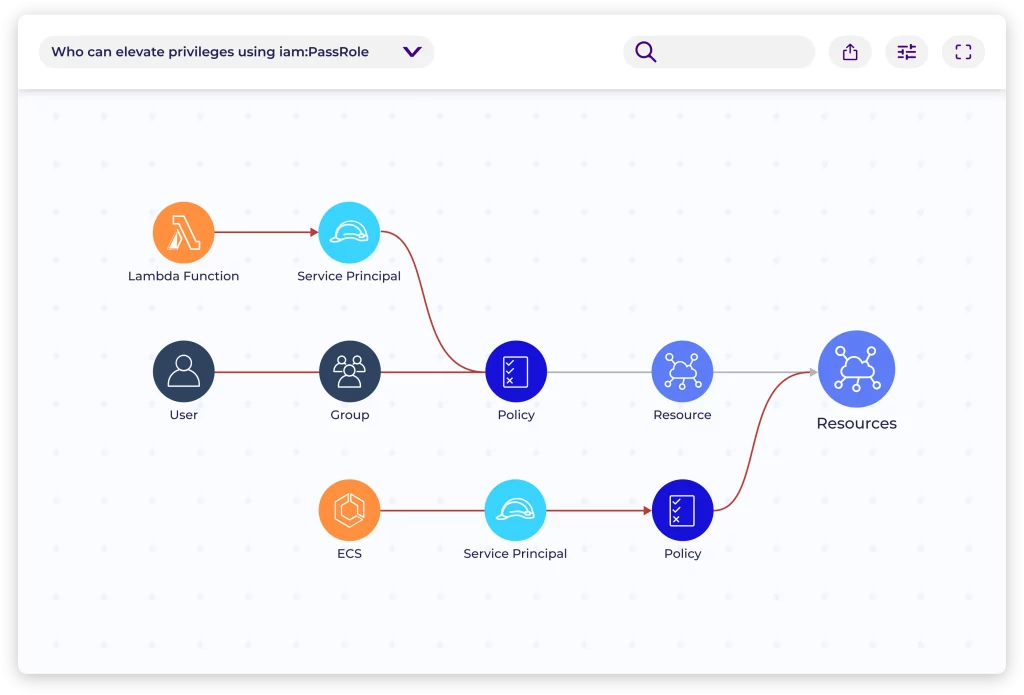
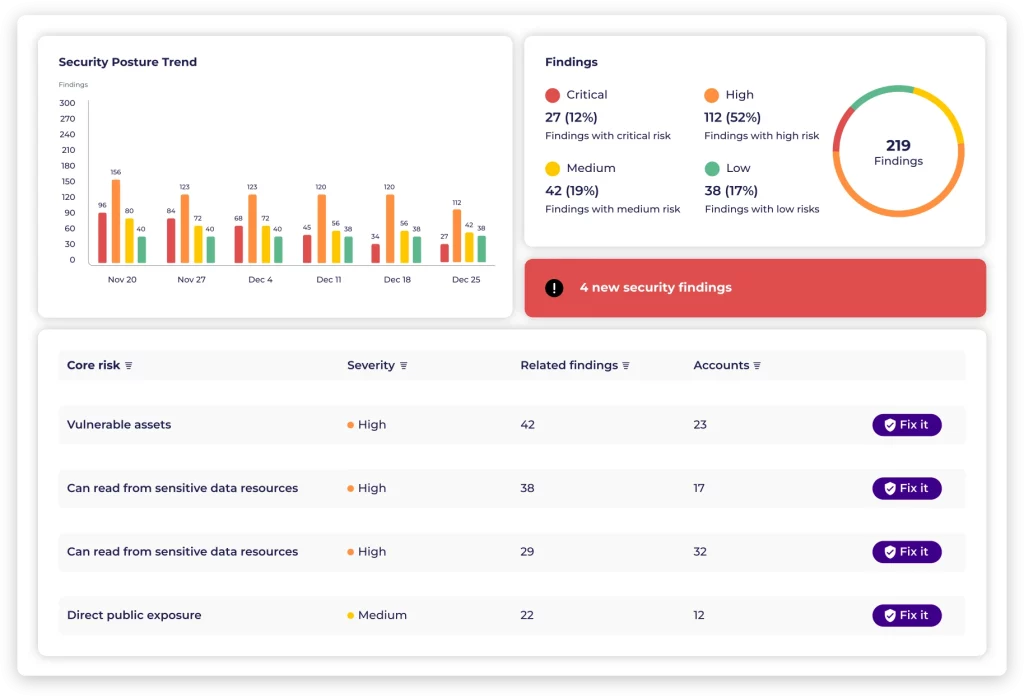
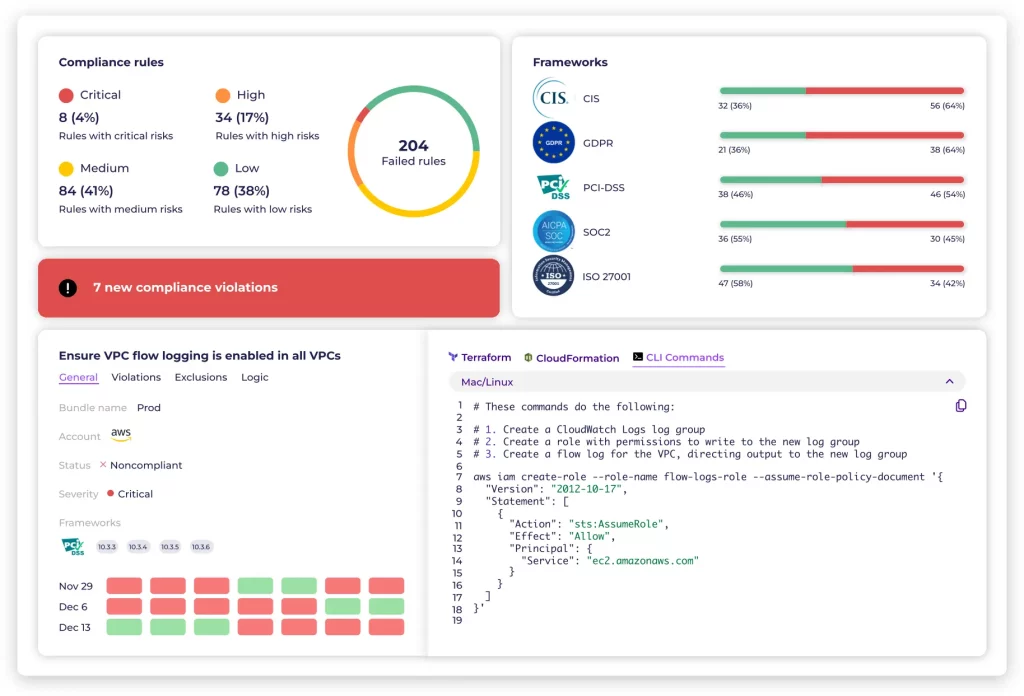
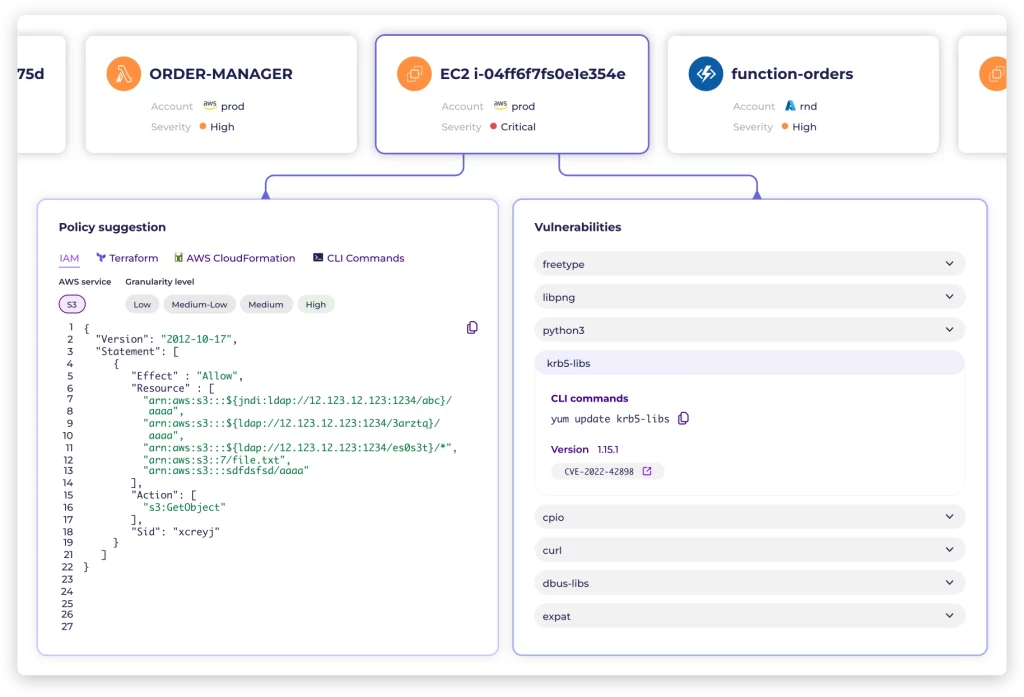
Empowering teams to proactively identify and prioritize cloud risks, fostering seamless collaboration among security, DevOps, and engineering.
Empower your cloud security team with Solvo’s unified platform. Bring everyone together to navigate threats, vulnerabilities, and compliance seamlessly. Elevate your security posture and stay ahead in safeguarding your digital assets.
Leveraging our automated remediation feature enhances engineering productivity, streamlines delivery processes, and bolsters overall security posture.




Embrace your preferred security and CI/CD stack. We’re here to seamlessly integrate, not dictate—making your work a breeze!

“Enhance threat detection through the integration of diverse data sources for comprehensive security insights.”

Eyal Zukovsky
CEO

We needed to prioritize security while maintaining seamless daily operations. Solvo empowered our team to concentrate on strategic objectives, and the true strength of Solvo lies in its seamless synchronization of security and operational requirements.

Daniel Neto
CISO

“We are very pleased with the way Solvo integrates with new, emerging technologies. From a security perspective, they deliver on the promise of improving the relationships between developers and security teams, helping them work together and be more productive.”
João Paulo Senatore
Head of Strategy and Partnerships

We needed to prioritize security while maintaining seamless daily operations. Solvo empowered our team to concentrate on strategic objectives, and the true strength of Solvo lies in its seamless synchronization of security and operational requirements.

Hilik Paz
CTO

“Compliance is so much easier now with simple access to Solvo’s reporting tools. A compliance audit is no longer a reason to worry about how long it will last or how difficult it will be.”
Discover and address cloud risks effectively and empower your security team with the autonomy they need.
Or explore on your own time with a free trial