Last week a Twitter user Arkady Tetelman shared that Zoom had an outage due to a misconfiguration of an AWS SCP for their DynamoDB. This is a sad but important example as to how a misconfiguration could cause business disruption and not only a cyber crisis.

In this blog we will learn more about SCPs, why they are important and how to utilize them, and how to check they were set properly.
Service Control Policies (SCP) are an essential part of AWS Identity and Access Management (IAM). SCPs provide a mechanism for organizations to establish controls over the services and actions that can be taken in their AWS accounts.
SCPs are used to limit the permissions of IAM users and roles to a subset of the permissions granted to the account, and they can also be used to restrict the ability to modify IAM policies and roles.
What are Service Control Policies?
SCP is a type of IAM policy that enables you to define rules for the entire AWS account or for specific AWS Organizations units. SCPs act as guardrails, ensuring that only authorized actions are taken in the account.
SCPs define the maximum permissions that can be granted to a user or role within the account, meaning that even if an IAM user or role has permissions to perform certain actions, SCPs can be used to restrict those actions.
SCP policies are defined in JSON format and can be attached to an AWS Organizations root or an Organizational Unit (OU). Once an SCP is attached to an OU, it applies to all the accounts that are a part of that OU.
SCPs can be used to limit access to AWS services, restrict access to specific resources, and prevent IAM users from creating or modifying IAM policies and roles.
What are SCPs Used for?
SCP is an essential tool for organizations that require a high degree of control over the actions taken in their AWS accounts. They provide an additional layer of security by limiting the permissions of IAM users and roles to a subset of the permissions granted to the account. SCPs can also be used to enforce compliance with regulatory requirements and industry standards.
For example, suppose an organization has multiple AWS accounts for different departments, and they want to ensure that each department can only access the resources that they need to do their jobs. In that case, they can use SCPs to limit the services and actions that each department can access.
Similarly, if an organization has compliance requirements that mandate specific security controls, such as restricting access to certain types of data, they can use SCPs to enforce those controls.
SCPs can also be used to prevent IAM users from creating or modifying IAM policies and roles, which can be useful in ensuring that only authorized users are allowed to make changes to the IAM policies and roles.
Why are SCPs Useful?
SCP is useful for organizations that need to establish controls over the services and actions that can be taken in their AWS accounts. SCPs enable organizations to create a standardized set of permissions that can be applied across all their AWS accounts, ensuring that all users and roles are working within the same set of rules.
By using SCPs, organizations can also reduce the risk of human error, as they can ensure that IAM users and roles are not granted excessive permissions or permissions that could lead to security vulnerabilities. SCPs can also help organizations to meet compliance requirements by providing a mechanism for enforcing security controls.
How to Utilize SCPs for Architecture Best Practices?
When using SCPs, there are several best practices that organizations should follow to ensure that they are getting the most out of this powerful tool.
- Start with a Plan: Before implementing SCPs, it is essential to have a plan in place. Organizations should identify their specific security and compliance requirements and develop a set of SCPs that align with those requirements.2.
- Use Least Privilege: SCPs should be designed to enforce the principle of least privilege. Only the minimum permissions necessary to perform a particular action should be granted. This helps to reduce the risk of accidental or intentional misuse of permissions.
- Test and Review: SCPs should be thoroughly tested and reviewed before being implemented. Organizations should test their SCPs in a staging environment to ensure that they are working as expected.
- Monitor and Update: Monitor and audit your AWS environment regularly to ensure that your SCPs are working as intended. Use CloudTrail logs to monitor user activity and check for any unexpected behavior.
How to check you configured SCP correctly?
We know that going over every SCP ever generated in your account doesn’t make sense and doesn’t scale, that’s why Solvo now supports these policies and analyzes them in addition to all other policy types we already analyze. This guarantees an every-updating, accurate security posture status and on time alerts about misconfigurations that could cause business disruption or security breaches.
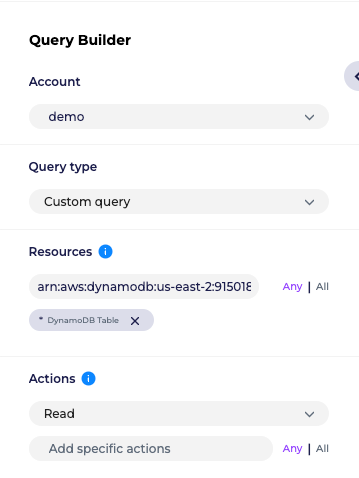
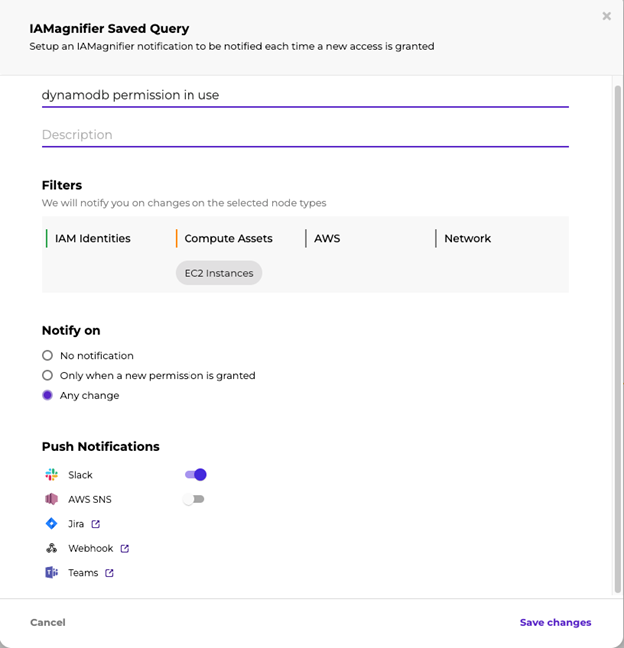
In order to check your SCPs as part of your security posture, use Solvo’s IAMagnifier, and build a query. We will look at an example that is similar to the Zoom DynamoDB issue.
- Build a query that checks for read permissions from any or a specific DynamoDB
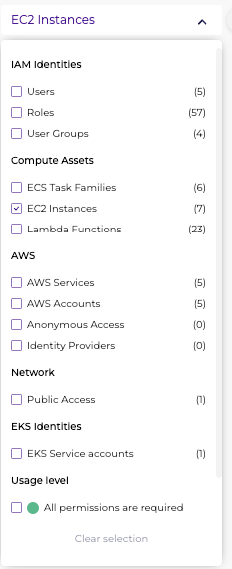
- After running the query you will get all assets that can read data from a DynamoDB table – in order to filter for specific types of asses for example EC2 instances use the filter option:
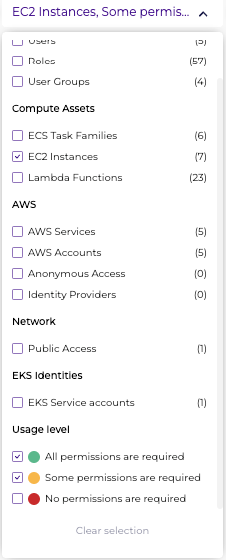
- Filter for the permissions that are being used, under the “usage level” filter
- Save this query and turn on notifications, to get notified for any changes, updates in this permission, access to the DynamoDB and even get notified if a permissions is being used for the first time, or if it has been revoked.
To check your SCPs and your security posture, start a FREE trial with Solvo here.