Data breaches
As public cloud environments become more complex, the number of potential vulnerabilities increases, making it easier for cybercriminals to exploit them and gain access to sensitive data.
Security value-added resellers (VARs) are facing a major shift in their business due to the rapid adoption of public cloud services. As organizations move more and more of their workloads to the cloud, VARs must adapt their offerings or risk being left behind. However, if VARs can take advantage of this transition, they can reap many benefits that will help them succeed in today’s digital economy.
The first major shift that security VARs are facing is the move from an on-premise to cloud-based offerings. This means that the traditional model of selling third-party software, hardware, and networking products is no longer sustainable.
To remain competitive, security VARs must be able to take advantage of the increased agility that cloud-native services provide. Since cloud services are updated frequently with new features and capabilities, VARs can quickly update their offerings to keep up with the changing needs of their customers. This allows them to keep their products and services up-to-date, and ensure that they remain relevant amidst the digital transformation movement.
Organizations are facing an increased level of complexity as they move towards their cloud-first digital transformation strategies. This complexity is becoming difficult to manage, driving the demand for security VAR services. As businesses continue to expand their cloud environments, they often reach a point where their existing cyber security practices simply cannot keep pace with the frequent changes to applications, the underlying infrastructure, and the increasingly intricate web of dependencies between them. Coupled with the rapidly evolving threat landscape, the complexity of public cloud environments introduces several security risks, including:
As public cloud environments become more complex, the number of potential vulnerabilities increases, making it easier for cybercriminals to exploit them and gain access to sensitive data.
With a complex environment, there’s an increased likelihood of misconfiguration of security controls, which can create security gaps and increase the risk of data breaches.
As the number of users with access to cloud resources grows, so does the risk of insider threats. Malicious or careless employees can inadvertently or intentionally cause security breaches.
Public cloud environments rely heavily on APIs, and any vulnerabilities in these APIs can lead to unauthorized access to cloud resources and sensitive data.
Complex cloud environments can make it difficult to maintain compliance with industry regulations and data privacy laws, increasing the risk of fines and legal action.
To mitigate these risks, organizations typically look to implement security best practices such as access controls, encryption, data protection, and security audits. Additionally, demand is rising for security automation tools that can help reduce the risk of misconfiguration and insider threats.
However, many organizations don’t possess the required resources to modernize their security posture along these lines. Implementing and maintaining advanced cloud security controls requires deep know-how, significant financial resources, and expertise that’s often expensive and hard to find.
In particular, protecting the public cloud infrastructure against unauthorized access involves complexities that are extremely difficult to understand and mitigate without the proper know-how. Under the shared responsibility model, the cloud service provider is responsible for the security of its infrastructure, while the customer is responsible for the security of its own applications and data running on it. This means that the customer is in charge of cloud infrastructure resource configuration, data encryption, access permissions and entitlements, and more.
Due to the complexity and dynamic nature of cloud environments, ensuring that users, applications, and services can access only the data and resources they are allowed to use (i.e., least privilege) is a challenge that even experienced security staff often struggle with.
In a large-scale cloud environment, access policies and controls must be constantly adapted to prevent unauthorized access to sensitive data and resources. Organizations that lack relevant cloud security expertise may be more likely to make configuration errors such as leaving databases or storage buckets exposed to the public internet. This is one of the main reasons that misconfiguration is one of the most common causes of security breaches in public cloud environments
Furthermore, in the event of a security breach or incident, organizations must be able to respond quickly and effectively to contain the damage and prevent further compromise. However, lack of expertise can hinder an organization’s ability to respond effectively to security incidents.
By working with security VARs, organizations gain access to a range of value-add services, including consulting, implementation, monitoring, and support, allowing them to customize their cybersecurity measures to fit their individual needs.
Security VARs have a deep understanding of the technology landscape and can advise customers on which solutions best meet their objectives. In addition, they provide value-added services using third-party tools, helping customers save time and money by allowing them to quickly identify and address security threats on their own.
Security VARs can differentiate their offerings by partnering with innovative security vendors. This can give security VARs access to new technologies and features that they can incorporate into their services. With these partnerships, security VARs can offer even more robust solutions that meet the needs of their customers.
Ensuring secure access to the public cloud infrastructure is a key area of focus for security VARs. High-profile cybersecurity breaches where misconfigured cloud infrastructure resources exposed sensitive data to unauthorized access and misuse have raised awareness of the importance of implementing effective access policies and controls.
As organizations continue to adopt best practices to protect their evolving cloud environments, many of them are seeking help from VARs to address this concern. To meet customers requirements, VARs are expected to bring innovative, comprehensive solutions that will enable organizations to move forward with their cloud strategies while ensuring that their infrastructure is adequately protected.
Solvo takes a different approach to cloud security that enables VARs to offer advanced cloud infrastructure security services.
Solvo supports security teams with the ability to automatically uncover, prioritize, mitigate and remediate cloud infrastructure access risks. Using multi-dimensional, contextual monitoring and analysis of infrastructure resources, applications, and user behavior, as well as the data associated with them, Solvo allows for implementing adaptive least privilege access policies and controls at scale.

Solvo automatically creates customized, constantly-updated least privilege access policies based on the level of risk associated with entities and data in the cloud, identifies and prioritizes risks, and proactively mitigates cloud misconfigurations and vulnerabilities.
Solvo’s unique platform gets to work right away in three distinct stages:
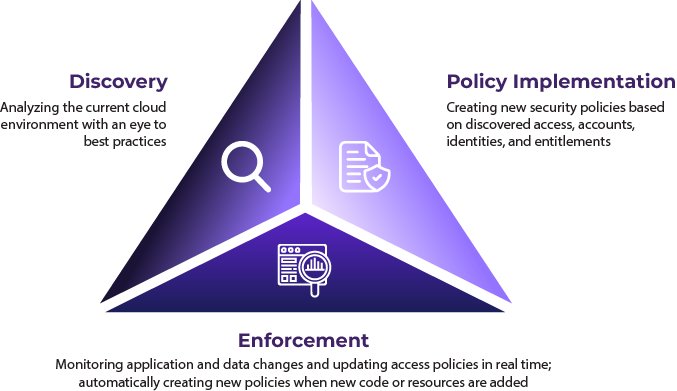
Overall, the transition to cloud-native services is a major change for security VARs, but it also presents a wealth of opportunities. By taking full advantage of these new opportunities, VARs can ensure that they remain competitive and successful in the digital economy. With the right strategies and partnerships, security VARs can continue to offer innovative solutions that meet the needs of their customers and help them succeed in today’s cloud-driven world.
The difficulty of protecting the cloud infrastructure against unauthorized access will remain a top security concern going forward. Leveraging their knowledge and expertise gained from working with a variety of organizations across different industries, VARs can have a major role in helping customers mitigate the complexity of implementing effective access policies and controls to secure their data and assets in the cloud.
By partnering with Solvo, VARs can offer customers a novel approach to cloud infrastructure security that bridges customers’ skills and resource gaps. Providing advanced automation capabilities based on contextual visibility into applications and user behavior, cloud infrastructure resources, and the data associated with them, Solvo can help VARs gain a critical competitive edge, and maximize the value they provide to customers.
Discover and address cloud risks effectively and empower your security team with the autonomy they need.
Or explore on your own time with a free trial