Who has access to my sensitive S3 bucket?
Who can create new IAM users in our account?
Who can read data off of my DynamoDB?
These are questions we often hear from security teams that are looking to enhance their governance and visibility into their cloud security posture. We also hear those questions from security auditors, who issue SOC2, ISO and other certifications.
Answering these questions should be fairly straightforward. The only problem is that the native cloud providers did not create an easy interface to help you answer the questions.
How can you analyze your IAM permissions on a graphDB?
One option is to inspect everything asset by asset, look into the security permissions and try to read between the (JSON) lines. In that case, even if you manage to find a security issue – how would you fix it?
Do you know what the least-privileged permissions are? Can you write a new policy by yourself? If so, good for you! Now go ahead and do it to the other 999 assets in your account.
Another option would be to use Solvo’s IAMagnifier. As they say: a picture of your security permissions is worth a thousand hours. Using the analyzer you can ask your questions and get the exact answer.
Who has access to your Bucket? Here’s a map of users and resources who can dig into your data. Who is at risk of being exploited for privilege escalation (Hi SolarWinds)? Here’s the treasure map.
The Magnifier’s map will show you a shortcut for least-privileged permissions, should you need one. On the map, excessive permissions are highlighted, and an alternative security permission is suggested.
The suggestion is based on the real behavior of your application, so there’s no worry of breaking the functionality of the app. All you have to do is enforce the new permissions and finally feel relieved.
Let’s take a look at at a few of the popular queries are users are running:
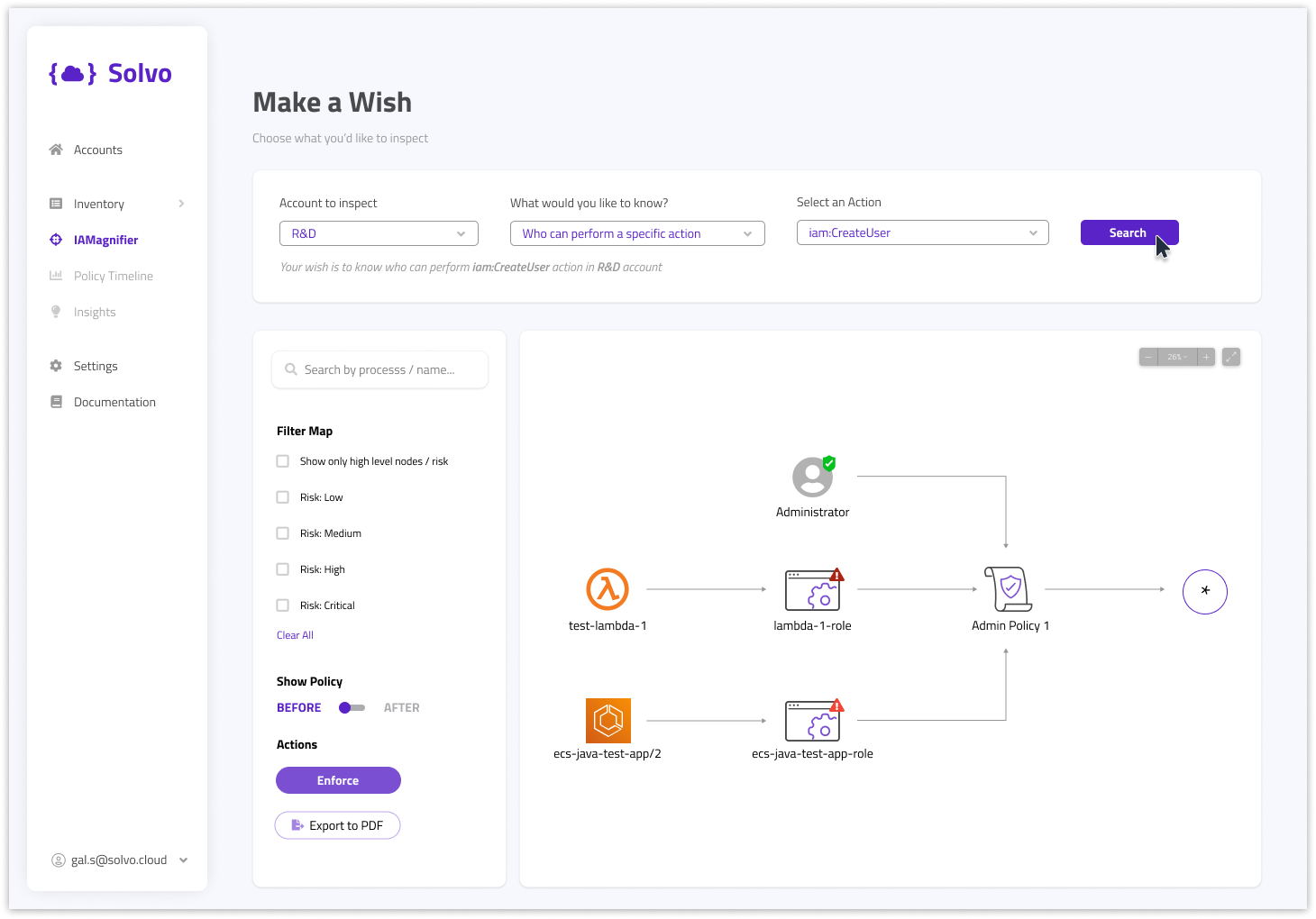
(1) It’s best practice to restrict the entities that can create new AWS users to specific Admin users. You’d be surprised to see who can create such users in your account. In Solvo’s IAMagnifier screen, you can easily ask the question, like this:
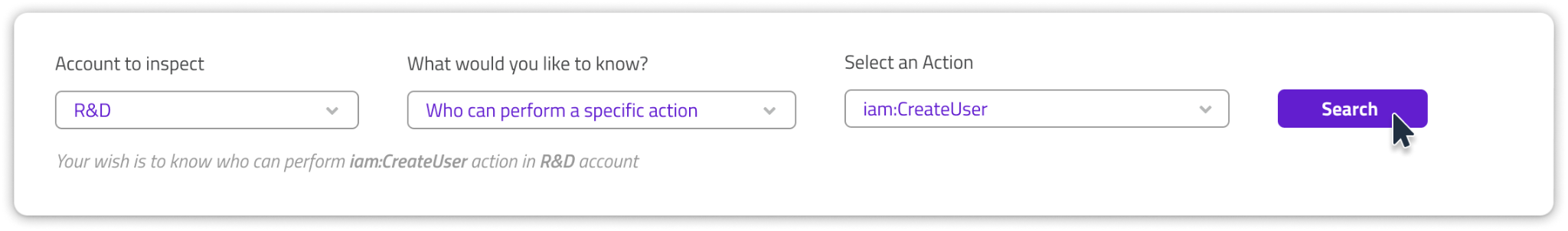
In this case, we see that other than the Administrator, there are several other cloud entities who can create a user.
So if they get compromised, a malicious insider could take advantage of this, create a user for themselves and have persistence in your account.
The red and green icons on the role node, mark the severity of the finding, and by clicking on the node, you will find the new policy Solvo’s engine had created for that entity.
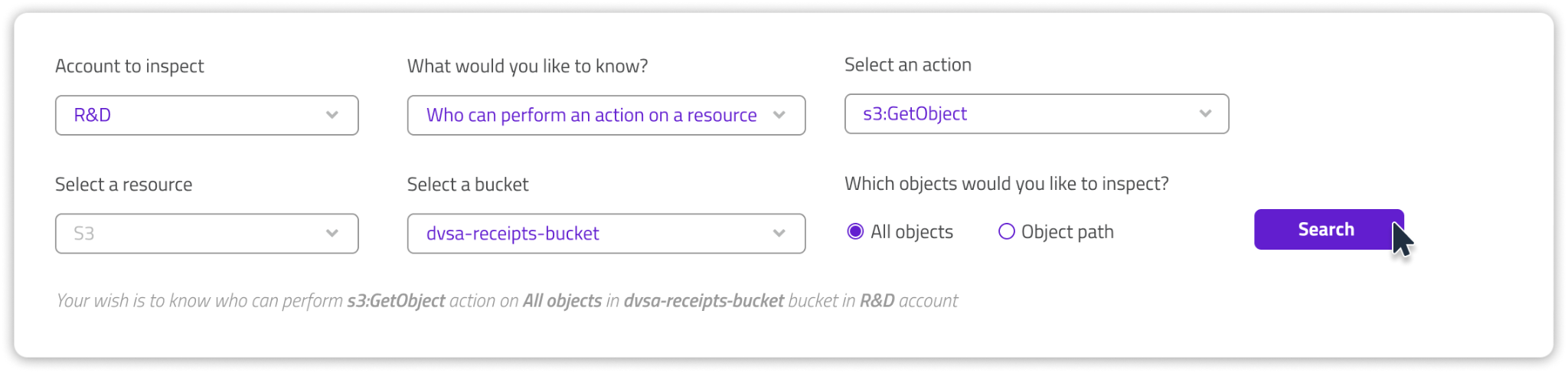
(2) S3 Bucket is the most popular cloud service in the world. It’s quick to spin, easy to use and available to just about anyone with internet access.
When used to store sensitive data, PII or anything else you find valuable, you must make sure only relevant entities are entitled to successfully run the S3:GetObject action.
Solvo IAMagnifier can help by showing you who can run this action on any or all your buckets, and recommend the least-privileged security policy that fits your scenario.
On the IAMagnifier screen you can ask your check and see if unnecessary entities can read your sensitive data.
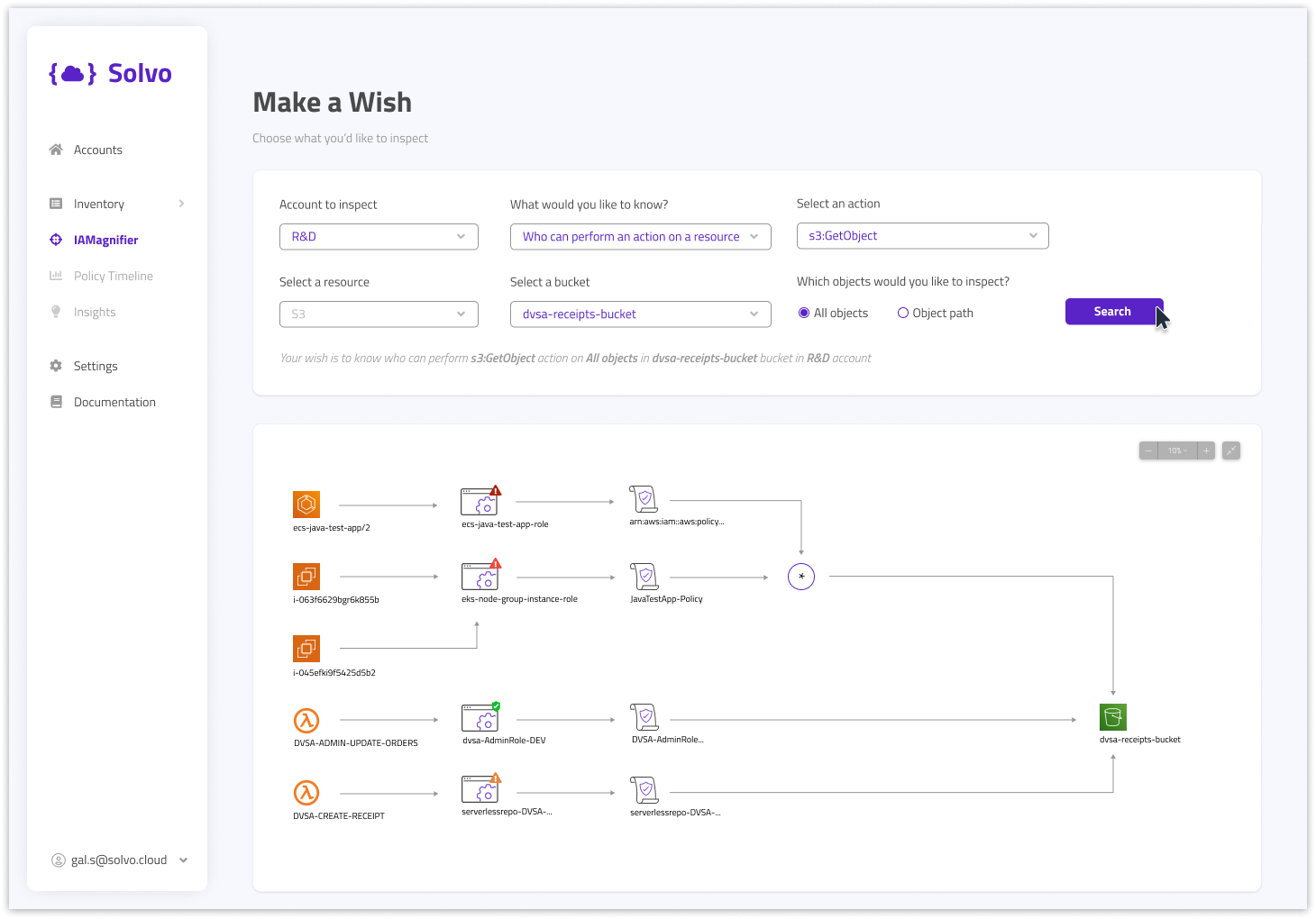
This is what the result might look like:
In this example, we see that 5 different cloud assets can put an object into the bucket, but only one is well-configured and least-privileged. We can also see that there are different paths to get to the bucket, using different roles and policies.
These paths are not easy to track, but the IAMagnifier makes it easy and comprehensible. By clicking each misconfigured role, Solvo helps you to enforce a newly created and least-privileged policy, that would make all the excessive permissions go away.
These are just a few examples out of the endless queries Solvo’s IAM Magnifier can run.
If you would like to know who (user or asset) has access to one of your cloud resources, and to reduce that number with just a click, schedule a demo below.