
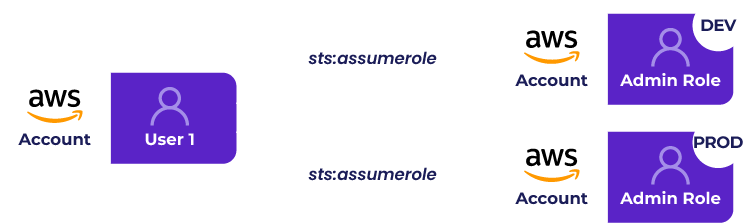
Last year, a new junior developer joined one of the engineering teams. Rather than giving permission to assume the admin role in the development account, the DevOps engineer in charge of creating new accounts accidentally granted permission to the new employee to assume the admin role in the production account. As part of the training, the developer created and made changes to the infrastructure in the AWS account. Having access to the production account, the developer mistakenly connected to the production account and carried out the training there. During the training, the developer accidentally deleted an AWS CloudWatch subscription filter that sends log records to an external application performance monitoring (APM) system. As a result, an alert was triggered in the monitoring system. The operations team investigated the alert and found out that the developer deleted the integration. To mitigate this vulnerability, the operations team revoked the developer permissions and granted permissions only to the development environment.

This incident lasted 4 days. Fortunately, the APM tool created an alert about the change, and the operations team was able to resolve the issue before the system was affected. However, the incident exposed the company to a significant risk as during this time, since the developer could have made changes in the production account that could have affected service availability and data confidentiality.
Following the incident, the customer decided to implement a solution that would identify and provide alerts on issues such as misconfigured access permissions as soon as they occur. A key requirement was the ability to get real-time alerts while minimizing false positives to enable the operations team to focus on the most critical vulnerabilities.
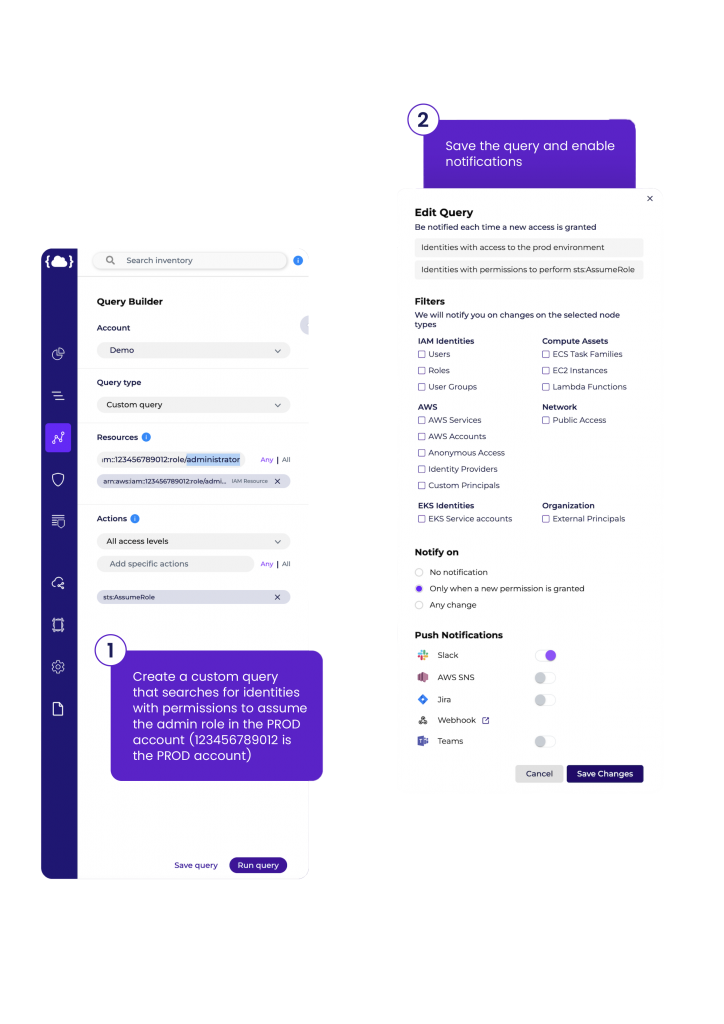
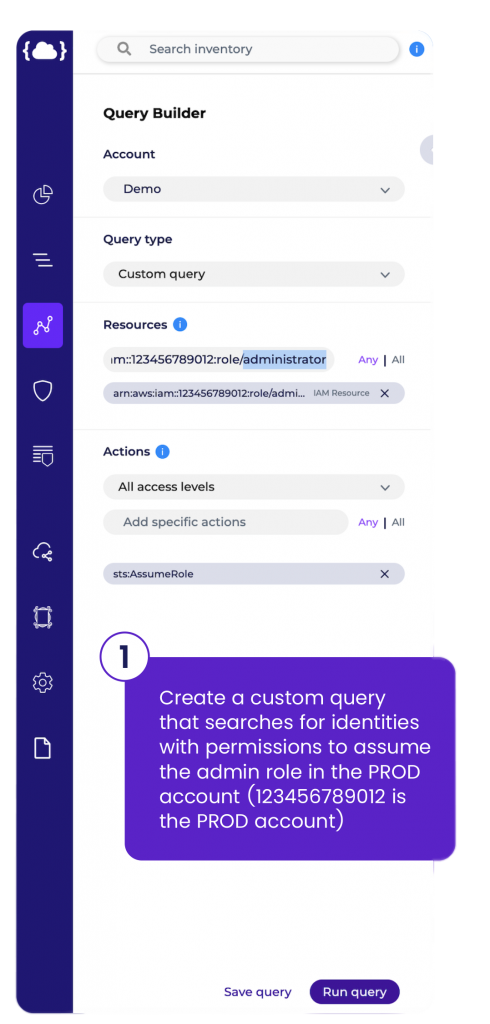
The customer chose Solvo’s IAMagnifier for its ability to provide accurate, contextual visibility into the cloud environment. Using IAMagnifier, it was able to identify who has permission to execute the sts:assume role action for roles in the PROD environment, investigate and restrict how this permission is used, identify users with excessive permissions, and much more.
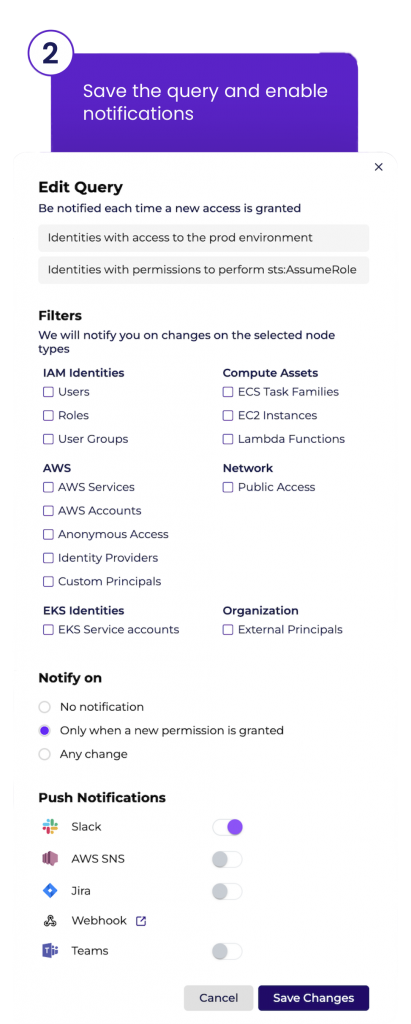
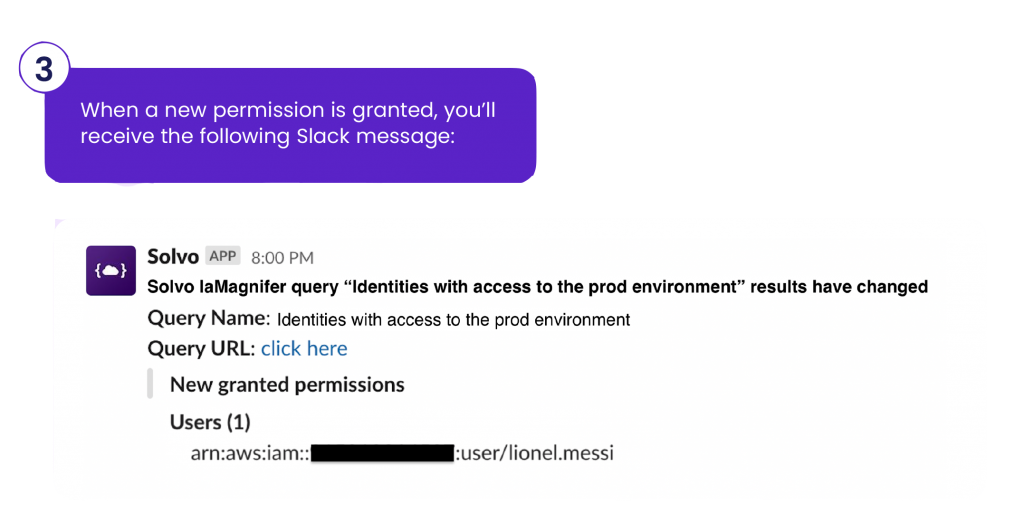
To prevent similar incidents from occurring in the future, an alert was created to notify the operations team (via Slack, Email, SNS, webhook, and more) when a user in the master account is given permission to assume a role in the production account.
According to the company’s Head of Operations, with IAMagnifier in place, “the incident could have been resolved in minutes instead of days, reducing the risk of affecting the service availability or exposing sensitive data.”
By using IAMagnifer, the customer was able to gain visibility into its expanding cloud infrastructure. It can now run queries and create graph-based maps of users, cloud resources, and access policies, identify chains of permissions, continuously identify risky, unused or excessive permissions, and easily adjust or create least-privileged access policies accordingly.
Due to Solvo’s multi-dimensional, contextual monitoring and analysis of infrastructure resources, applications and user behavior, and the data associated with them, the customer can identify and prioritize vulnerabilities based on their exploitability and potential impact, and resolve them in a timely manner.
Discover and address cloud risks effectively and empower your security team with the autonomy they need.
Or explore on your own time with a free trial